Ultimate guide to IoT device security

From smart TVs and speakers to security cameras and door locks, Internet of Things (IoT) devices are now part of everyday life at home and at work. Each one collects data, connects to the internet, and, if poorly secured, can quietly widen the attack surface of a whole network.
IoT device security matters whether you’re protecting a home network or managing a larger deployment. This guide explains the main ways connected devices can be exposed and offers practical steps to reduce those risks. It shows how to think about device and network protection together and how to best configure settings and access controls.
What is IoT device security?
IoT device security refers to the methods and tools that protect connected devices, such as sensors and smart appliances, from unauthorized access and data theft. It focuses on keeping each device secure throughout its lifecycle, from manufacturing and setup through to its operation and future updates.
Why IoT devices are especially vulnerable
Many IoT devices still don’t offer the same built-in security and long-term support as traditional IT hardware. Combined with the way these devices are deployed (always on, network-connected, and often less closely monitored than laptops or servers), this leaves IoT ecosystems with a broad, persistent attack surface that attackers can exploit.
Learn more: Read our detailed guide on IoT connectivity.
How device security differs from network-level protection
Both device-level and network-level security are vital for keeping IoT systems safe.
| Device-level security | Network-level security | |
| Focus | Protects the individual IoT device, its firmware, and stored data | Protects communication and traffic between devices, servers, and systems |
| Key methods | Secure boot, firmware verification, strong authentication, and data encryption | Firewall, virtual local area network (VLAN), intrusion detection system, and network segmentation |
| Goal | Prevent unauthorized control or tampering of individual devices | Stop threats from spreading across networks and prevent external breaches |
| Scope | Operates at the device level, handling security for each endpoint | Operates at the infrastructure level, managing how devices interact |
| Example | Performing a secure boot so only trusted software can run | Using a firewall to block malicious network traffic |
Common security risks for IoT devices
Knowing these risks will help you find weak points and put stronger protections in place before problems happen.
Weak or default passwords
Many IoT devices come with easy-to-guess default passwords. If these aren’t changed, attackers can use them to gain quick access and take control of devices. Updating default credentials with strong, unique passwords reduces this risk.
Insecure communication channels
IoT devices are constantly sending and receiving data from apps, servers, and other systems. If these connections don't have the right encryption, attackers may be able to access critical information as it travels across networks. Insecure channels can also allow attackers to inject malicious data or commands.
Firmware vulnerabilities and lack of updates
Firmware is the built-in software that runs on IoT devices and controls their core functions. When it contains coding errors, outdated components, or misconfigurations, it can introduce security flaws that attackers can exploit.
Many IoT devices receive infrequent or no firmware updates, which means known vulnerabilities can remain unpatched for years. Without a reliable update mechanism, the security of connected devices tends to degrade over time due to the discovery of new vulnerabilities.
Physical tampering and reverse engineering
IoT devices often sit in accessible locations, which makes them easy targets for physical tampering. Attackers can access these devices, take out memory chips, or alter circuitry to steal data or find out how the gadget works.
This kind of hands-on analysis is known as reverse engineering: taking a device apart or examining its hardware and firmware to understand how it operates. When attackers do this, they may uncover encryption keys, hardcoded access credentials used by companion apps and client software, or details of proprietary communication protocols.
With that information, they can gain unauthorized access and control of the device, imitate trusted devices, decrypt captured traffic, or design attacks that scale beyond a single compromised gadget.
Learn more: Find out more details in our articles about IoT cybersecurity and IoT attacks.
Best practices for device-level security
Following established best practices helps reduce vulnerabilities and keeps devices operating safely and reliably throughout their lifecycle.
Local device logs and forensics
Logs record events such as login attempts, configuration changes, and data transfers on a device. When an issue or breach occurs, these records make it easier to see what happened and when.
Forensic tools (in this context, specialized software and techniques used to collect, preserve, and analyze digital evidence) can then work with log data to trace how an attack unfolded and identify compromised components. Keeping logs protected and backed up helps ensure there is reliable evidence available for investigation and response.
Software and firmware updates
Software and firmware updates fix known bugs and security issues in IoT devices. Security baselines like the European Telecommunications Standards Institute’s EN 303 645 treat timely security updates and secure update mechanisms as key manufacturer responsibilities. The European Union Agency for Cybersecurity (ENISA) similarly stresses the need for regular patching over the often long lifetime of IoT devices.
Where possible, enable automatic updates so devices receive fixes without the need for manual intervention. If that isn’t available, set a regular time to check for and install updates as part of a routine maintenance schedule.
Secure configurations
Many IoT vulnerabilities stem from human error. The IoT Security Foundation calls for “no universal default passwords,” and ENISA documents insecure or hardcoded credentials and unnecessary functions and services exposed to the public internet as common IoT attack paths.
To reduce risk, change factory-set passwords during setup (where possible), disable features and remote access options you don’t need, and follow the security recommendations in the manufacturer’s documentation. Reviewing device settings from time to time helps make sure they stay aligned with your security needs as your network and usage change.
VPN integration for IoT device security
A virtual private network (VPN) encrypts data between the VPN endpoint and the VPN server. In a home setting with a commercial VPN, that endpoint is usually the device running the VPN. However, many smart home IoT devices (such as smart bulbs, speakers, and thermostats) can’t run a VPN client. To secure them, you’ll typically need to rely on a VPN-enabled router.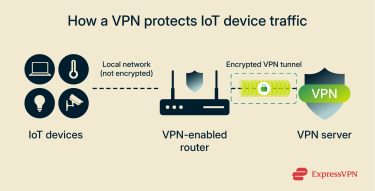
In these setups, traffic between an IoT device and a router still travels over the local network, while the VPN (like ExpressVPN) encrypts traffic from the router to the VPN server. This secures the data in transit from on-path observers, such as cybercriminals, on the wider internet.
Because the local hop isn’t part of the VPN tunnel, man-in-the-middle (MITM) attacks can still occur on the local network. VPNs also can’t prevent attacks that originate from other devices on the same network.
Site-to-site VPNs for industrial IoT scenarios
A site-to-site VPN is a type of VPN that securely connects two or more whole networks rather than individual devices, using an encrypted tunnel between their gateways. This can be a good fit for industrial IoT environments where multiple facilities need to exchange data securely over untrusted links.
Instead of running a VPN client on each device, gateways at each site handle the secure connection. Sensors, controllers, and other operational systems send their traffic through these gateways, which then forward it through the encrypted tunnel.
For example, a factory and a remote control center can share production metrics and automation commands without exposing that data to the public internet. Properly configured site-to-site VPNs reduce the risk of eavesdropping and tampering, though they still need to be combined with strong access control and network segmentation.
Core pillars of IoT device protection across large infrastructures
As IoT deployments grow into full-scale IoT infrastructure spanning devices, gateways, and cloud services, the focus shifts from securing individual devices to managing identity, access, and data across entire fleets. The following pillars are important for organizations that run large, interconnected IoT environments and need consistent, scalable defenses.
Strong authentication
Strong authentication verifies that every device and user accessing an IoT system is legitimate. Multi-factor authentication (MFA) adds extra layers of verification, such as one-time codes, and its implementation is highly recommended.
Regularly changing passwords and encryption keys further reduces risk; the less time a given password or key is in active use, the less time cybercriminals have to crack or otherwise compromise it. Together, these measures make it much tougher for hackers to take over IoT devices.
End-to-end encryption and encryption at rest
Encryption converts data into unreadable ciphertext to prevent unauthorized access. End-to-end encryption (E2EE) ensures that data is encrypted on the sender’s device and stays encrypted while it travels across networks or through cloud services, so only the intended recipient’s device can decrypt it.
This prevents intermediaries like service providers, attackers, or compromised servers from reading the information in transit.
Encryption at rest is a separate but complementary protection. It ensures data stored on servers or devices are encrypted, so even if someone gains access to the storage system, the data remains unreadable without the proper keys.
E2EE and encryption-at-rest, when combined with robust key management, provide strong protection against interception, theft, or unauthorized access across the full lifecycle of IoT data.
Secure APIs and device interfaces
APIs and device interfaces allow IoT devices to communicate with apps, users, and other systems. If these connections aren't secure, cybercriminals can use them to steal data or take control of IoT devices.
Secure APIs use authentication, encryption, and strict access permissions to prevent misuse. Regular testing and patching of these interfaces keep communication channels safe and ensure devices only interact with trusted systems.
Device identity management and allowlisting
Each IoT device should have a unique digital identity to confirm its legitimacy within a network. Device identity management assigns and verifies these credentials, preventing counterfeit or unauthorized devices from connecting.
Allowlisting gives you even more control by only letting pre-approved devices join or communicate on the network. These measures limit exposure, block rogue devices, and help keep data exchange within trusted parts of the IoT infrastructure.
Role-based access control (RBAC) for devices
RBAC limits what users and systems can do based on their roles. For instance, a technician might have permission to update the firmware of a device but not access the data stored on it.
RBAC lowers the chance of accidental data exposure or malicious activities by giving people only the access they need to perform specific tasks. When you apply this principle to IoT devices, it makes them easier to control and less likely to do damage if someone compromises a relevant employee’s account.
Advanced IoT device security strategies
Critical IoT ecosystems may require greater security measures. Advanced techniques leverage new technologies and frameworks to keep devices safe, improve communication, and find threats before they can do any damage.
These technologies help companies and developers make defenses that are smarter and more flexible, so they can keep up with the complicated cyber hazards of today.
Implementing zero trust for device authentication
Zero trust for IoT systems assumes no device or user is trustworthy by default. Every connection request must prove its identity before gaining access. In an IoT setting, this means continuously verifying each device, even those that are already connected to the network, using strong credentials, certificates, or behavior-based checks.
This method stops attackers from moving about freely after they break into one device and makes sure that only verified devices can communicate with each other.
Protocol-level hardening for embedded systems
Embedded systems (small, dedicated computing units built into devices) use communication protocols like Message Queuing Telemetry Transport (MQTT), Constrained Application Protocol (CoAP), and File Transfer Protocol (FTP).
Attackers often look for flaws in these protocols to intercept or alter data. For example, FTP is a legacy protocol that transmits data without encryption, so when it appears in embedded systems (often for backward compatibility), it should be replaced with or secured by modern, encrypted alternatives.
Protocol-level hardening strengthens how these systems communicate by enforcing encryption, authentication, and integrity checks. In practice, this often means using secure transport layers such as Transport Layer Security (TLS), for example, MQTT over TLS, or secure web protocols like HTTPS, instead of sending data in plaintext.
Updating firmware regularly and turning off protocol features that aren’t needed also makes the device less likely to be attacked and more reliable overall.
Lightweight cryptography for resource-limited devices
Many IoT devices have limited processing power and memory, making traditional encryption too heavy to run efficiently. Lightweight cryptography protects data effectively while utilizing minimal resources, allowing for secure communication and data storage without significantly affecting device performance.
Implementing lightweight encryption makes it possible for even small, battery-powered sensors to keep critical data safe in large, distributed IoT networks.
AI/ML for real-time threat detection
AI and machine learning (ML) can process huge amounts of IoT data to identify unusual patterns or behaviors that indicate an attack. For instance, they can detect when a device starts transmitting abnormal traffic or communicating with unknown servers. Real-time analysis allows systems to block suspicious activity right away, minimizing damage and downtime.
Building a security strategy for IoT deployment
A well-planned IoT security plan makes sure that businesses can safely use devices and protect data across the network. Whether for small businesses or large enterprises, having structured processes, clear policies, and proactive monitoring reduces vulnerabilities and helps teams respond effectively to threats.
Conducting a security audit of existing devices
Start by reviewing all connected devices to identify current security gaps. A security audit examines device configurations, firmware versions, credentials, and network access. The results highlight vulnerabilities and provide a baseline to measure improvements, helping organizations decide what steps to take first and track their progress.
Creating a risk-based IoT asset inventory
It's crucial to have a complete inventory of all your IoT devices. Sort gadgets by how risky they are, the sensitivity of the data they handle, and how they link to the internet. This method makes sure that devices with a higher risk are secured accordingly and that devices with a lower risk are still monitored properly.
Risk-based inventory helps businesses use their resources efficiently and acquire a holistic view of the whole IoT ecosystem.
Defining a device security policy
A security policy outlines rules and expectations for all devices in the network. It should cover password requirements, software updates, network access permissions, and approved configurations. Clear rules ensure consistent protection, reduce misconfigurations, and define standards for employees, vendors, and system administrators.
Selecting security tools and platforms
Choose tools and platforms that monitor, protect, and manage IoT devices. Enterprise-level solutions can find threats, automatically patch issues, and verify devices. Choosing good security software makes sure that your devices stay up to date and that you get notifications right away when something goes wrong.
Training employees and enforcing cyber hygiene
Human error remains a major cause of IoT security breaches. Training employees regularly teaches them safe practices, like changing default passwords, identifying phishing attempts, and following update schedules. Encouraging excellent cyber hygiene across teams lowers the chance of inadvertent data exposure or misconfigurations.
Incident response and recovery planning
It’s important you know what to do in case of a breach. An incident response plan specifies who acts, what actions are taken, and how to communicate internally and externally. Regularly testing the strategy will ensure that in a real scenario, containment happens quickly, damage is kept to a minimum, and recovery happens faster. By planning ahead, IoT security goes from being reactive to proactive.
Device lifecycle and decommissioning best practices
Managing IoT devices from the time they are installed until they are retired is important to keeping security strong. Following best practices at every step lowers risks, stops data breaches, and makes sure that devices don't become entry points for cybercriminals.
Secure onboarding of new devices
When adding new IoT devices to a network, verify their authenticity and configure security settings immediately. Change default passwords, enable encryption, and install the most recent firmware updates before connecting them to other systems. Automatic updates should also be turned on if available. Secure onboarding makes sure devices start their lifecycle in a protected state, minimizing vulnerabilities from the outset.
Handling lost or compromised devices
Devices that are lost, stolen, or compromised constitute an urgent security risk. Implement processes to quickly isolate these devices from the network and revoke their credentials. Remote wiping or locking features can help keep important data safe, while monitoring solutions can identify suspicious activity before it spreads to other devices.
Secure disposal and data wipe procedures
When you retire IoT devices, make sure to securely wipe all of the data on them so that no one else can get it back. Physically destroy the storage part if you need to, then follow the manufacturer’s instructions for how to get rid of it safely.
Decommissioning retired devices makes sure cybercriminals can’t exploit them as a backdoor into an IoT network.
Learn more: Check out our article on IoT public safety.
FAQ: Common questions about IoT device security
How do I secure my IoT devices at home?
To secure your Internet of Things (IoT) devices, change the default passwords, update the firmware often, and put them on a different network from your other important systems. Set up multi-factor authentication (MFA), use strong, unique passwords (if it’s possible to change them), and give each device access only to what it needs.
What’s the role of encryption in IoT device protection?
Encryption keeps data safe by making it unreadable unless it’s decrypted with the correct key. It can protect data from being intercepted while it’s moving between devices and servers (in transit) and while it’s being stored (at rest).
What is MFA, and how is it used in IoT?
Multi‑factor authentication (MFA) requires two or more verification methods before it grants access to a system. In Internet of Things (IoT) settings, MFA makes sure that even if a password is stolen, access to a device is still protected by another factor, like a smartphone app or biometric data.
Which protocols are considered secure for IoT devices?
Many Internet of Things (IoT) deployments rely on Transport Layer Security (TLS) to protect data in transit. For example, Message Queuing Telemetry Transport (MQTT) over TLS or HTTPS can encrypt the connection between devices and servers and support proper authentication, which helps prevent eavesdropping and tampering.
How often should IoT firmware be updated?
You should update Internet of Things (IoT) firmware whenever security patches or critical fixes are released. When you delay updates, you leave your devices exposed to vulnerabilities attackers can use to compromise them.
Can offline IoT devices be hacked?
Yes, cybercriminals can compromise offline Internet of Things (IoT) devices if they gain physical access.
How does a VPN improve IoT device security?
A VPN encrypts internet-bound traffic between the VPN endpoint and the VPN server. This makes it harder for external observers to see or tamper with communications involving Internet of Things (IoT) devices.
However, a VPN doesn’t encrypt traffic on the local network or fix issues like weak passwords, missing updates, or insecure default settings on IoT devices.
What's the difference between VPN and TLS in IoT?
Transport Layer Security (TLS) secures specific communication channels between devices and servers, while a VPN creates an encrypted tunnel between a VPN endpoint and a VPN server, with all traffic routed through that tunnel being protected as it crosses untrusted networks.
In other words, TLS protects particular sessions at the application layer, while a VPN protects a broader network path and can reduce how visible a device’s traffic is to outside observers.
How do consumer and industrial IoT security needs differ?
Industrial Internet of Things (IIoT) security needs to consider workplace safety regulations like those from the Occupational Safety and Health Administration (OSHA), which focus on preventing hazards that could affect worker safety or equipment operation. In contrast, consumer IoT security focuses primarily on protecting personal data and home networks.
What IoT devices are most vulnerable to home attacks?
Devices that run outdated firmware, lack security update support, use factory-set passwords that can’t be changed, or expose unmanaged cloud interfaces are generally the most vulnerable to home attacks.
How do I lock admin settings on my smart devices?
It’s common for smart devices not to support full admin lockout, and many have only one account, meaning an attacker could lock out the owner if they gain access. The best approach is to change default passwords, disable unnecessary remote management features, and enable multi-factor authentication (MFA) where available.
These steps help protect remote access, but they can’t stop someone with physical access from resetting or reprogramming the device.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN