IoT in public safety: Applications and impact

The Internet of Things (IoT) is transforming how cities approach public safety. Connected sensors, cameras, and communication systems can detect fires, floods, and accidents in real time, improving response times compared with traditional phone calls and manual reporting. At the same time, integrating these technologies comes with technical, logistical, and security challenges.
In this article, we’ll examine how IoT supports public safety, the technology that powers it, the obstacles cities encounter, and the role of secure connectivity in keeping these networks protected.
What is IoT in public safety?
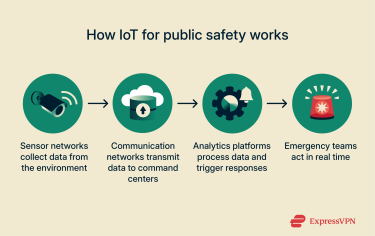
IoT in public safety uses connected devices such as sensors, cameras, and smart vehicles to detect issues and share real-time information with emergency teams. It operates through three fundamental components:
- Sensor networks: A group of devices that collect data from their surroundings, such as temperature, air quality, movement, or structural stress. In public safety, that can mean detecting smoke, gas leaks, flooding, or changes in traffic patterns that signal a problem.
- Communication networks: Once the sensors gather data, they automatically send it to the appropriate parties for immediate action. This connection can run on cellular, Wi-Fi, or other secure network types, depending on the setup.
- Analytics platforms: These systems analyze the incoming data to decide what action to take. They might trigger an alarm, alert responders, or even send notifications to residents if there’s a fire, flood, or accident nearby.
Key technologies involved
Several technological threads make IoT public-safety systems possible:
- Edge computing and networks: Some IoT sensors, cameras, and nearby gateways can process data on the spot to reduce delays, which is known as edge computing. Edge networks support this by linking these close-by devices so information moves through local nodes instead of traveling to a distant cloud.
- Connectivity and architecture: The communication networks that link IoT devices to command centers and to one another across large distances.
- AI and machine learning: AI and machine learning analyze the data collected by IoT devices. They can recognize patterns, detect unusual activity, and predict possible risks.
Real-world applications of IoT for emergency response
Many IoT technologies for public safety are still in development. However, there are major cities around the world that have already begun using them in pilot programs as they transform into smart cities.
Faster response through connected devices
Connected devices can reduce the time between when an emergency occurs and when help arrives. Here are some ways smart cities utilize IoT to remain proactive during critical situations.
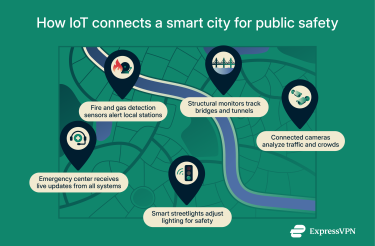
- Fire and gas detection: Smart sensors in smart homes and public spaces can quickly detect smoke or gas leaks and automatically alert local fire departments.
- Early infrastructure warnings: Sensors placed on bridges, tunnels, and public buildings can monitor structural integrity. If they detect cracks or other issues, an alert goes out to the construction teams so they can take care of the issue before it becomes dangerous.
- Automated alerts from connected cameras: AI-powered video systems analyze footage to spot potential threats, such as unattended bags or unusual crowd movement, and notify authorities to investigate immediately.
Location-based alerts and smart dispatch
Beyond detecting emergencies sooner, IoT also helps cities respond more intelligently. Location-based systems and connected infrastructure guide responders along the safest, fastest routes and ensure the right teams get deployed where they're needed. Here are some of the ways such developments can happen.
- Smart traffic systems for clear routes: IoT-enabled traffic lights like those in Marietta, Georgia, can change patterns to give ambulances and fire trucks priority access, cutting precious seconds or even minutes off response times.
- Real-time dispatch optimization: Technologies like the Advanced Mobile Location (AML) protocol help pinpoint the exact site of an incident, helping dispatchers send the nearest available unit.
- Connected surveillance for situational awareness: Cameras equipped with recognition technology, such as those in Lucknow, India or the facial recognition vans used by U.K. police, can help identify suspects or emergencies and share live data with nearby patrols.
- Public transport monitoring: IoT data from buses and trains helps responders track large crowds or disruptions, assisting emergency access even during rush hour.
How smart sensors can save lives
Smart sensors turn critical information into action. Two large-scale IoT deployments show how this technology is already improving emergency response worldwide.
In the U.S., over 22,000 first responder agencies use the RapidSOS intelligent safety platform. It links over 600 million IoT devices, from phones and wearables to connected vehicles and home sensors, directly with 911 and field responders. When a device detects an emergency, it sends verified data such as location, crash details, or health metrics straight to dispatchers. In commercial fire scenarios, agencies piloting RapidSOS Digital Alerts with Emergency24/Hexagon have reportedly cut the dispatch step from around 2.5 minutes to about 13 seconds by sending alarm data directly to 911, bypassing phone calls.
In the EU, eCall automatically alerts emergency services after a serious car crash. Each equipped vehicle quickly transmits key data, such as time of impact, location, and vehicle identification number. On impact, the system initiates a voice connection between the vehicle and the nearest emergency call center, so responders can assess the situation directly, even if the driver is unconscious or unable to speak.
According to the European Commission, this technology reduces average response times by roughly 40% in cities and 50% in rural areas and reduces the number of fatalities by at least 4% and the number of severe injuries by 6%.
Both systems demonstrate that when IoT networks combine real-time data with reliable infrastructure, they can make emergency response faster, more precise, and more coordinated.
Cybersecurity considerations for IoT devices in public safety
Despite the clear benefits of IoT in public safety, these devices are especially vulnerable to cybersecurity risks and raise significant privacy concerns due to their connectivity, large scale, and constant monitoring of real-world conditions.
Device-level vulnerabilities
Large attack surface
IoT devices used in public safety create a wide attack surface. Each device introduces its own software, connection, and potential vulnerabilities, which gives attackers many places to look for weaknesses.
Compounding this, public safety networks often consist of hundreds or thousands of interconnected sensors, cameras, and communication systems. A single compromised device can potentially provide a foothold for attackers to move laterally, access sensitive data, or even disrupt emergency response operations.
Limited built-in security
Many IoT devices offer only minimal built-in security because they’re designed to be small, inexpensive, and easy to deploy. This can mean weak default passwords, limited authentication options, and basic or outdated encryption (or no encryption at all).
Some devices don’t receive security patches regularly, and others can’t be updated at all. Attackers can take advantage of this by targeting models known to have flaws that never get fixed.
Legacy devices
Some IoT devices used in public safety were designed years before today’s security standards, which leaves long-standing vulnerabilities in place. Legacy sensors and cameras can run on outdated communication methods or hard-coded settings. Since their weaknesses are well documented, they’re easier for attackers to identify and exploit.
Device lifecycle
IoT devices pass through a long lifecycle that includes manufacturing, deployment, daily operation, and eventual end-of-support. Weaknesses can appear at any stage. Some devices rely on third-party code or hardware that may contain unpatched flaws. If those components were never vetted, attackers can exploit them later. Others stop receiving updates after only a few years. If they remain connected, these unsupported devices can become long-term points of exposure.
Data collection and handling risks
Overcollection of data
IoT devices used in public safety can capture far more information than the situation requires. A camera meant to detect movement may also record identifiable individuals, and an environmental sensor may pick up background audio. The more data IoT devices collect, the more sensitive information is at risk and needs to be protected. Also, such information makes a single breach more damaging than it would otherwise be.
Unclear data pathways
Data from IoT devices rarely travels in a straight line. It may move through local edge processors, network gateways, cloud platforms, analytics tools, and third-party systems before reaching emergency dashboards. If these paths aren’t fully mapped or monitored, it becomes challenging to understand where the data lives, who has access to it at each stage, and which parts of the pipeline are most at risk. This lack of visibility raises the chances that a weak link will go unnoticed.
Excessive data retention
Some IoT deployments store data for far longer than necessary, often because retention settings are left at defaults or because clear policies are missing. Video footage, sensor logs, and location histories can accumulate quickly and create large data repositories.
The more data stored in one place, and the longer it stays there, the more attractive the system becomes to attackers. Large archives also increase the severity of any breach, since years of information could be exposed at once.
Third-party access
IoT ecosystems in public safety often rely on multiple outside providers, such as cloud hosting services, data analytics platforms, device manufacturers, or software vendors. Each one may apply different security standards, update schedules, or access controls.
If one of these partners has weak protections, attackers may target them instead of the primary system. Compromising the least secure party can still grant access to data flowing through the rest of the network, making third-party gaps a significant concern.
Cyber-physical risks
Because IoT devices interact directly with physical systems, a cybersecurity issue can quickly translate into real-world disruption. If attackers interfere with devices that monitor hazards like smoke, flooding, or structural stress, emergency alerts may be delayed or triggered based on false readings.
The role of VPNs in IoT public safety infrastructure
In IoT public safety systems, a VPN adds an extra layer of protection as data moves between devices, gateways, and command centers. A VPN encrypts traffic, essentially scrambling it to make it unreadable, which prevents information from sensors, cameras, and alert systems from being intercepted or altered while traveling over public or shared networks. Enterprise-level VPNs also support several other functions that help keep IoT-based public safety systems secure and reliable:
Access control and authentication
Enterprise VPNs can verify the identity of each device or user before allowing them onto the network. That prevents unauthorized sensors, rogue gateways, or compromised devices from slipping in and sending false data.
Secure communication across mixed networks
Public safety IoT deployments often span cellular, municipal Wi-Fi, leased lines, and third-party infrastructure. A VPN creates a consistent layer of security across all of them, so the underlying network type doesn’t affect data protection.
Safeguarding command-and-control systems
VPNs also secure access to dashboards, alerting platforms, and other control systems that coordinate emergency responses. Keeping these interfaces isolated from the public internet reduces the risk of tampering or intrusion.
However, it’s important to note that VPNs secure the communication channel, not the device. While VPNs are a strong tool for protecting data in transit, they do not secure an IoT device that’s already compromised, and they don’t replace endpoint hardening, secure boot, device attestation, or zero-trust access controls.
A VPN ensures that only authenticated devices can communicate, but if a device is infected with malware or running outdated firmware, the VPN can’t prevent that device from sending malicious or manipulated data through an encrypted tunnel.
FAQ: Common questions about IoT public safety
How does IoT improve emergency response times?
The Internet of Things (IoT) can shorten response times by speeding up both detection and action. Instead of relying on someone to notice a problem and call for help, connected sensors can identify emergencies the moment they happen and alert responders instantly. Once help is on the way, IoT-powered traffic systems can clear the path for ambulances by adjusting traffic lights in real time to get responders to the scene faster.
What are the 5 C’s of IoT, and how do they apply here?
The “5 C’s” of the Internet of Things (IoT) are connectivity, continuity, compliance, coexistence, and cybersecurity. These describe the essential principles for ensuring IoT devices and systems operate reliably, safely, and effectively. For example, a connected camera (connectivity) must stay online consistently (continuity), follow privacy regulations (compliance), work smoothly alongside other smart devices (coexistence), and be protected against hacking (cybersecurity).
How do smart cities ensure privacy with IoT?
To better protect citizens’ privacy, smart cities need to introduce regulations on the local government level and work with the tech companies developing these systems to ensure that the data is anonymized, can only be stored for a certain length of time, and has strict access controls. Transparency is equally important: residents should know what data is collected, how it’s stored, and how it’s used.
Do IoT devices used for public safety need a VPN?
A VPN isn’t required, but it’s one of the most effective ways to secure Internet of Things (IoT) communications. It encrypts data in transit and can restrict network access to verified devices. For systems that handle sensitive information, like surveillance feeds or emergency dispatch, VPNs add a strong layer of protection against unauthorized interception.
What are the benefits of using a VPN in smart surveillance systems?
VPNs encrypt video surveillance footage as it travels over the internet and prevent bad actors from intercepting the feed. They also authenticate devices before allowing them to connect, reducing the risk of spoofed cameras or unauthorized access. This is especially valuable in large-scale smart city environments where thousands of devices share data simultaneously.
Are there VPN alternatives for securing public IoT networks?
Zero-trust network access (ZTNA) or private 5G networks can also be used to secure communications. These VPN alternatives limit access to verified endpoints and often work alongside VPNs to create a layered defense strategy. Regardless of the chosen approach, encryption, regular audits, and strict authentication policies remain essential.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN