What is Trojan malware? Full guide to risks and protection

Trojans are a type of malware that trick victims into downloading their dangerous payload by masquerading as safe software or files. Depending on the specific threat, a Trojan may stealthily gather your sensitive personal data, hold your files for ransom, download additional threats, or cause damage in various other ways.
In this guide, we’ll explore what Trojans are, how they work, and the specific threats they pose to you and your devices. We’ll also cover signs of a Trojan infection to look out for and how to remove one from your computer or phone.
What is a Trojan?
Trojans are one of many subtypes of malware. Knowing what they are is an important piece of cybersecurity knowledge that everyone should have.
Definition of Trojan malware
Trojans (sometimes somewhat inaccurately referred to as Trojan viruses) are a type of malware defined by the fact that they pose as legitimate software or files. Beneath this veneer of security, they actually contain malicious code and can cause damage to your device once downloaded or installed.
In terms of appearance, Trojans may look like an update for an existing program, a free piece of software, or files like documents and movies. Unknown to the victim, the download contains malicious code.
Is a Trojan a virus or malware?
Technically speaking, Trojans and viruses are two distinct types of malware. Unlike viruses, Trojans don’t tend to replicate themselves or inject malicious code into other files.
Beyond that, any given Trojan will likely fall into another category of malware depending on the threat it poses. For example, a Trojan might also be a cryptojacker, a piece of ransomware, or spyware.
That said, many people use the word “virus” to refer to all types of malware, not just threats that self-replicate. In that less technical sense, a Trojan may be called a virus.
Key differences between Trojans and viruses
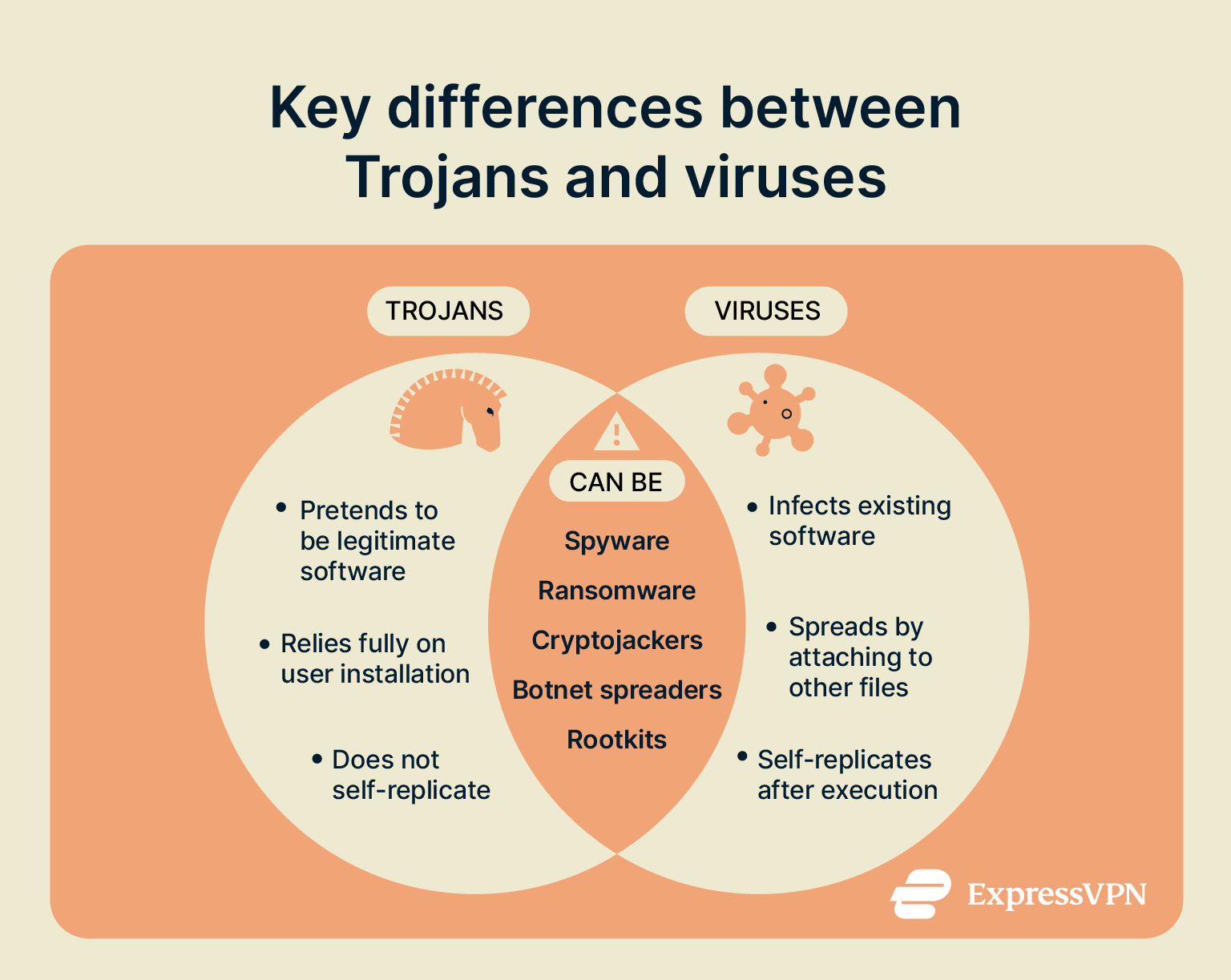 Trojans and viruses are both considered malware vectors. The two terms describe the way a threat is delivered, not the effect it has on a victim’s device. Behind the scenes, Trojans and viruses operate differently.
Trojans and viruses are both considered malware vectors. The two terms describe the way a threat is delivered, not the effect it has on a victim’s device. Behind the scenes, Trojans and viruses operate differently.
Trojans are designed to appear as a useful file or app. The aim is to trick users into downloading and fully installing the file. Once installed, most Trojans are stealthy and do not immediately appear to be dangerous. They may have a legitimate use in order to keep the victim from uninstalling the software. Additionally, many Trojans will alter the target device to make uninstallation more difficult.
In contrast, viruses often execute their attack as soon as the user opens the infected file. Unlike Trojans, viruses can reproduce by infecting other files on the device, spreading according to their programming. While viruses typically require the user to initiate the infection, they can then operate with more autonomy, whereas Trojans usually need the user to complete the full installation process before becoming active.
As malware vectors rather than specific threats, there is a lot of overlap in the damage that Trojans and viruses cause.
Brief history of Trojans
The name “Trojan” to describe deceptive malware comes from the legendary battle of Troy, which saw Greek armies give their Trojan enemies a large wooden horse as a supposed peace offering. Hours after the horse was let into the city, Greek soldiers who had hidden inside the horse came forth and ultimately conquered the city of Troy. As a symbol of deception, the word "Trojan" became attached to computer files that appeared to be safe but actually contained hidden threats.
It’s argued that John Walker coded the first Trojan in 1975. His Trojan, called PERVADE, created additional copies of a game called ANIMAL to help other users find the software. Though not innately malicious, this model would later be copied by cybercriminals to cause real harm.
An early example of a malicious Trojan comes from 1989. A computer programmer sent out floppy discs to attendees of a medical conference with accompanying letters explaining that the disc contained information about the ongoing AIDS epidemic. Opening the file presented victims with a harmless questionnaire. But after a device that had interacted with the disc was rebooted 90 times, the entire hard drive would be encrypted, resulting in a loss of data. A message would also appear telling victims to send cash to an address in order to recover their files.
This is an excellent example of a Trojan. It appeared entirely legitimate for a prolonged period but contained hidden ransomware code. Many future Trojans would employ similar strategies.
In the years since, Trojans have proved a highly effective method for spreading all manner of malware. They’re common on all kinds of devices, with seemingly legitimate mobile apps being a particularly widespread problem; xHelper, an Android Trojan, infected approximately 131 devices daily in its first seven months. While Trojans targeting iOS users tend to cause less damage than their Android equivalents, iPhones aren’t immune to this kind of threat.
How do Trojans work?
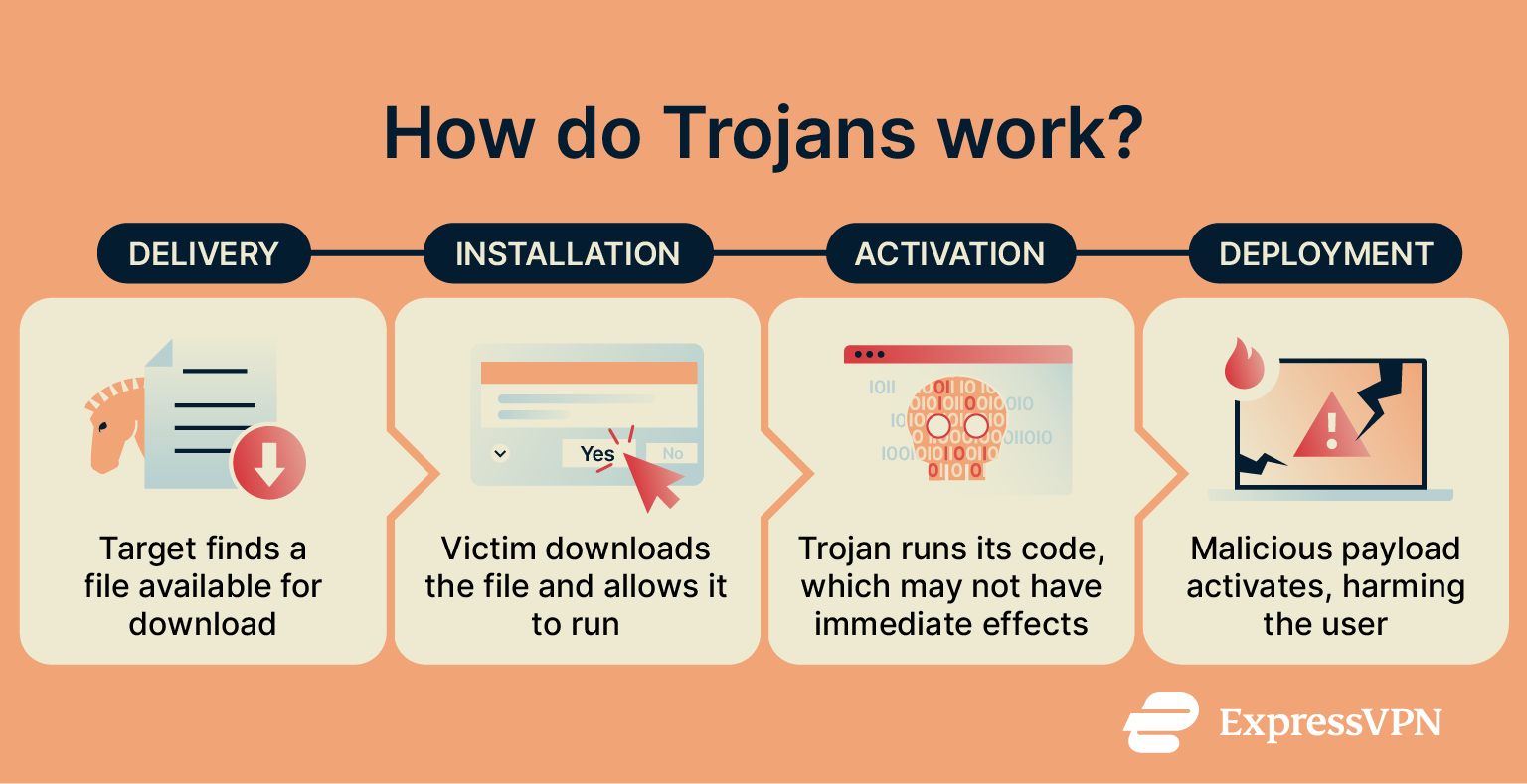 Cybercriminals distribute Trojans through a variety of methods, from posting them on file-sharing sites to spreading links over email, SMS, and social media.
Cybercriminals distribute Trojans through a variety of methods, from posting them on file-sharing sites to spreading links over email, SMS, and social media.
To trick users into downloading and installing Trojans, cybercriminals employ social engineering tactics. Social engineering is a broad set of practices that exploit human emotions to get people to act rashly. Fear and greed are often exploited alongside calls for immediate action.
Once a victim installs the payload, what happens next depends on what the specific Trojan was built to do. It may immediately take remote control of your device, discreetly spy on you, or steal sensitive information. Alternatively, the device may work normally until a set amount of time elapses or a specific action is taken.
Long-term consequences of Trojan infections
Trojan infections can have a number of long-term consequences, from one-time financial losses to identity theft. Remote Access Trojans (RATs) may give a cybercriminal full control of a user’s device without the victim realizing it for months or years. Personal data mined via Trojans and published on the dark web may follow a victim for the rest of their life. Similarly, data destroyed by a Trojan may be irrecoverable, resulting in months or years of lost work.
How Trojans spread across devices
Trojans rely on deception, with cybercriminals using a variety of techniques to convince users to download, run, and keep the malware installed on their devices. Before getting into the specifics, it’s worth noting the general social engineering tactics used to convince people to download files.
Exploiting human psychology to spread Trojans often involves:
- Preying on your curiosity: A common tactic is to make an outrageous claim or promise to share sought-after information. A strong desire to learn something can cause people to put their guard down.
- Pretending to be a celebrity or company: Just as Trojans imitate legitimate software, Trojan distributors often pretend to be famous figures and firms. For example, a message purporting to come from your phone company may include a fake bill or promise that you’ll get a discount if you download a new app, which is actually a Trojan meant to spy on you.
- Using someone else’s breached account: Cybercriminals often use hacked accounts to cause further damage. If a friend or colleague has had one of their accounts breached, they may send you messages that try to convince you to download a Trojan.
- Exploiting greed: Trojans are often spread by promising to provide something that’s normally expensive for free. Using a variety of platforms, cybercriminals offer cash, a lucrative job, or free software and media to convince users to download malicious software.
- Creating a false sense of urgency: Usually in tandem with the above strategies, scammers often send messages that demand urgent action. By pushing targets to act fast, scammers can convince people to do things they otherwise wouldn’t.
Employing the above tactics, cybercriminals use a number of platforms to spread Trojans.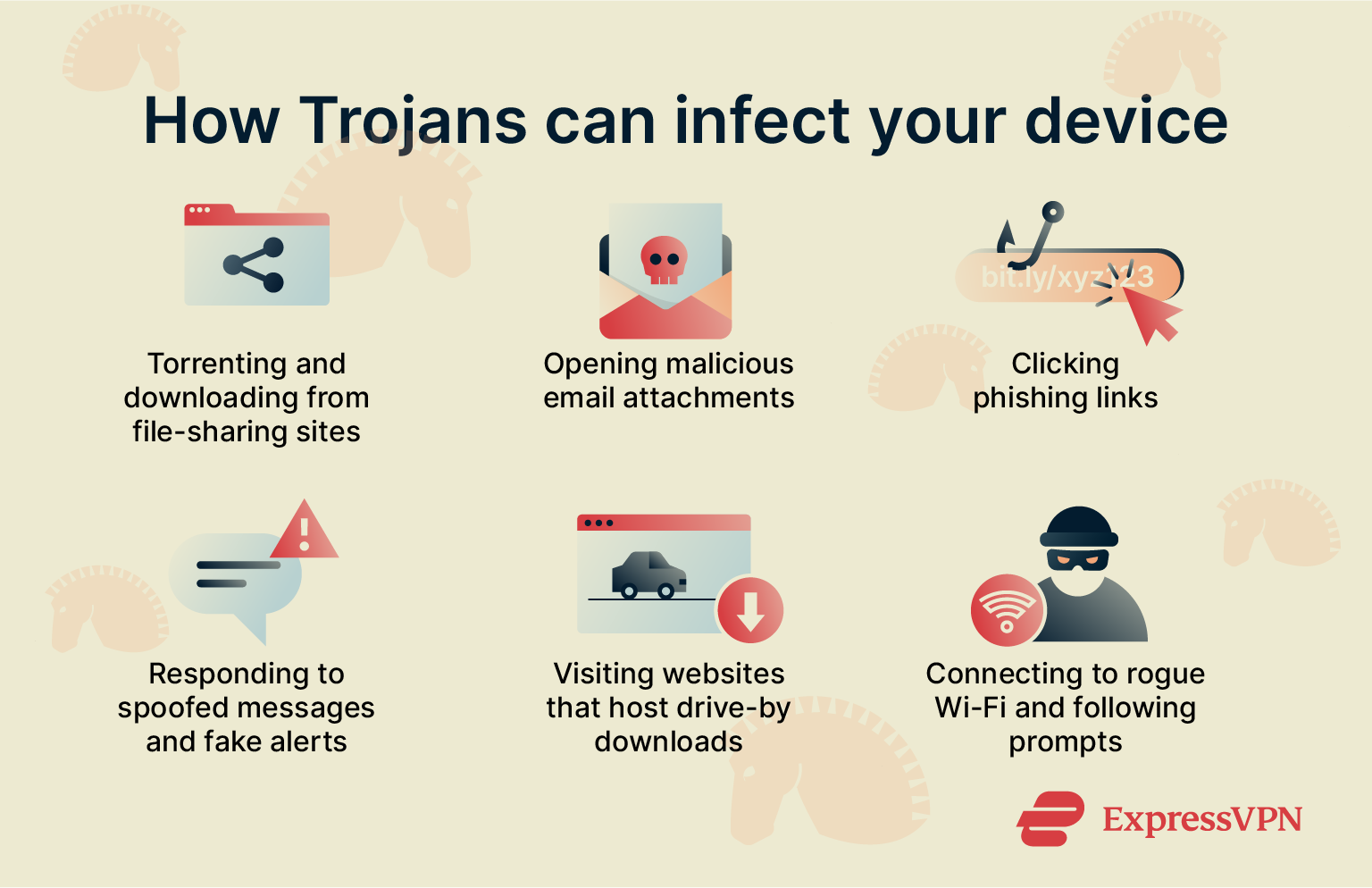
File-sharing sites and torrents
Internet users looking for free versions of paid applications, programs, and media often turn to file-sharing sites, which are rife with Trojans. This also happens on legitimate platforms. For example, Trojans spread on Telegram and Discord often masquerade as free games and movies.
Admins of these sites and channels may not always scan uploaded files for malicious code, which allows cybercriminals to freely upload Trojans. Sites without sufficient moderation may never take these files down.
Email attachments and phishing links
Cybercriminals can send Trojans as email attachments or distribute links to pages that host malware disguised as something else. Because threat actors know that people are less likely to open emails and links from an unknown sender, they often resort to impersonating public figures and legitimate businesses.
Spoofed messages and fake alerts
Malicious alerts on websites can be used to spread Trojans. These pop-ups are made to look like device notifications or message windows for popular platforms. Usually, they say that you’ve won something or that your device has been compromised (known as a scareware attack). In any case, these notifications will usually contain a link to a page where you can download a Trojan posing as an antivirus or a free program.
Infected websites and drive-by downloads
Trojans can also be delivered as drive-by downloads, files that download without the user clicking a download button or performing a similar action. Threat actors can spread drive-by downloads on websites they control, which could include legitimate sites that have been compromised.
It’s best to treat any file that downloads without your permission as suspicious, regardless of how reputable the site you were visiting is.
Hacked and malicious Wi-Fi networks
Cybercriminals have been known to create malicious networks in order to spread Trojans and other threats. For example, many passwordless public Wi-Fi networks require users to visit a captive portal authorization page before accessing the internet. These are normally perfectly safe, but threat actors could create such a page that points users to a page where they have to download a file in order to get online. Potentially, this could be a method for distributing Trojans.
Types of Trojan malware
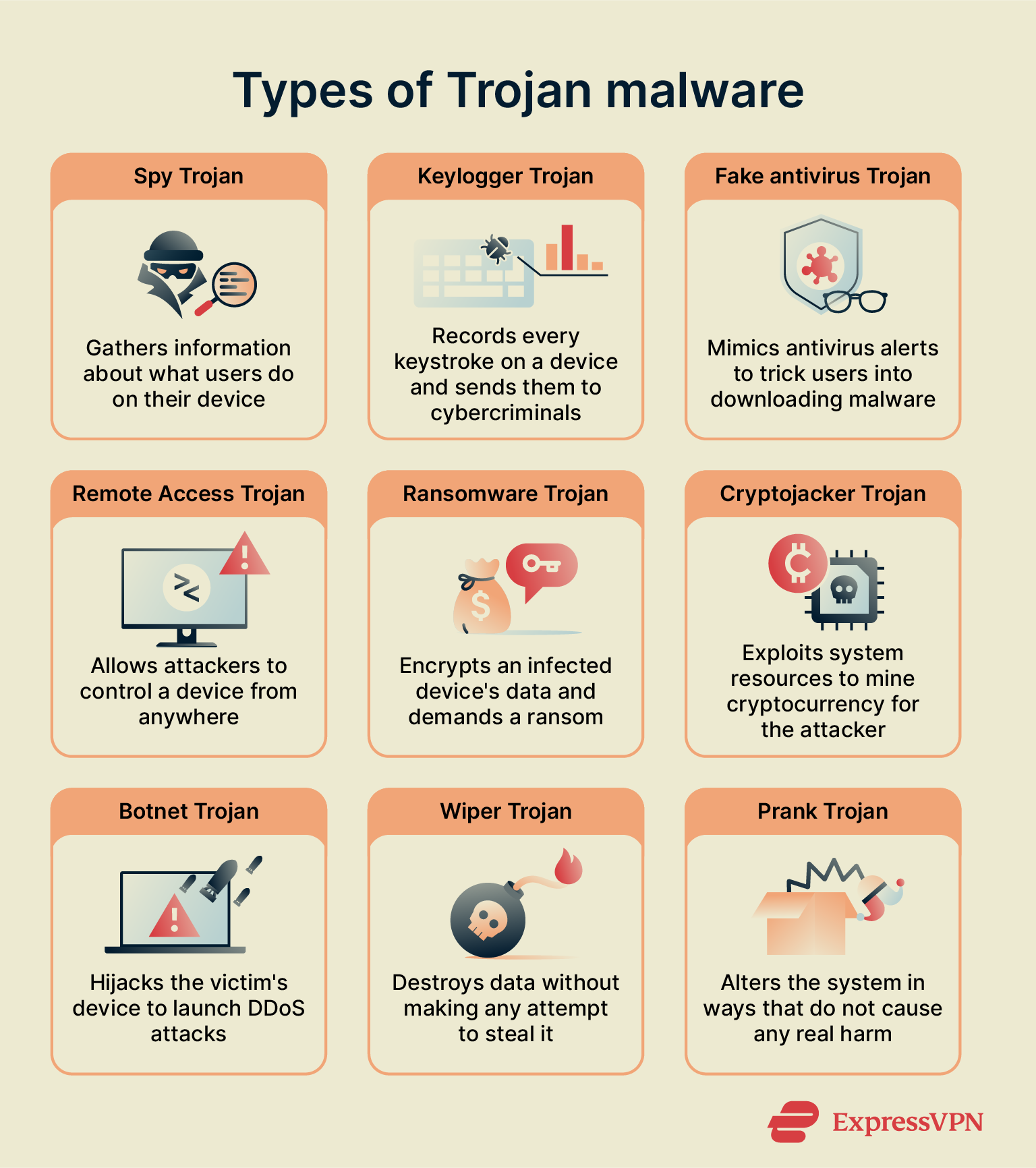 Though all Trojans disguise themselves as safe files and programs, the nature of the actual threat they pose varies quite significantly. Here are some of the common types of Trojans circulating today:
Though all Trojans disguise themselves as safe files and programs, the nature of the actual threat they pose varies quite significantly. Here are some of the common types of Trojans circulating today:
- Spy Trojans: Cybercriminals use spyware to record user activity, take screenshots, harvest emails, and monitor browsing activity.
- Keyloggers: A dangerous type of spyware, keyloggers harvest everything typed into the infected device’s keyboard and usually send the data to a threat actor.
- Fake antivirus Trojans: These Trojans prey on fear by mimicking legitimate antivirus alerts, warning users of a threat already on their device. They’ll prompt users to download a fake antivirus.
- Remote Access Trojans (RATs): Attackers use RATs to control a target’s device from anywhere, whenever it’s connected to the internet. They can change device settings (e.g., disabling your antivirus), modify files, and install additional malware.
- Ransomware Trojans: Often activated long after the malware has been installed, ransomware Trojans lock up data on a device. To regain control of their data, victims are told to pay a fee to the party responsible.
- Cryptojacker Trojans: Cryptojackers hijack a device’s computing resources in order to mine cryptocurrency, which is then sent to a cybercriminal’s wallet.
- Botnet Trojans: Exploiting a device’s networking capabilities, botnet Trojans recruit victims’ computers to join a network of infected devices. Cybercriminals use botnets to launch distributed denial of service (DDoS) attacks and other illegal acts, so a Trojan could lead to your device being used to strike an unrelated victim.
- Wiper Trojans: Wiper Trojans exist purely to delete critical data from a system without trying to steal anything. They may be used for sabotage, coercion, or vandalism.
- Prank Trojans: Some Trojans imitate legitimate software but don’t damage the device or spy on the target. Often, they simply make simple visual changes to the device. Though potentially annoying, these Trojans are relatively harmless.
Signs of a Trojan infection
The signs of a Trojan infection are similar to the red flags associated with other types of malware. Because Trojans can have a wide variety of effects, there are lots of possible symptoms to look out for.
Key indicators on your device
- Slow performance and crashes: Malware consumes system resources, and any device only has so much RAM to go around. This can lead to slow overall performance and poor response times when using normal applications.
- Unusual pop-ups or programs: Trojans may result in unusual programs or pop-ups appearing on your device. Watch out for anything you don’t recognize, and be particularly cautious of notifications demanding you take immediate action.
- Disabled security tools: Some Trojans may turn off your device’s security software in order to execute additional attacks. If you find that Windows Defender or a similar tool has been disabled, a Trojan could be responsible.
- Strange browser effects: Trojans often interfere with browsers. If you’re experiencing redirects to websites you didn’t intend to visit or notice new toolbars or extensions that you didn’t install, this could be the work of a Trojan.
How to detect and remove a Trojan infection
If you’re experiencing any of the above symptoms or believe you may have a Trojan for any other reason, you’ll need to confirm what you’re dealing with.
Using malware scanners
Download a trusted antivirus or pull up your device’s built-in security tools. Once you’ve made sure the software is up-to-date, run a full scan. You may want to run the scan in Safe Mode and disconnected from the internet to prevent a potential RAT from interfering with your attempt to remove the threat.
If the scanner detects any malware, it will usually provide information about the nature of the malware. It may identify the culprit as a Trojan. But whatever it finds, follow the software’s recommendation to quarantine and remove the threat.
Monitoring system performance
Monitoring for unusual activity may expose a Trojan. This method is less effective against Trojans designed to remain dormant.
Most OSs have built-in tools for monitoring performance and active processes. On Windows PCs, simultaneously press the Ctrl + Alt + Delete keys, then select Task Manager. If you’re on a Mac, search for and open the Activity Monitor to see a list of active processes.
It’s best to take these steps while you don’t have other programs open. Examine the list and look for anything that looks suspicious, paying particular attention to processes that are using a lot of resources. If you find something unusual, it could be related to a Trojan. Look up the name of anything you’ve singled out as suspicious and see if you can find more information.
Checking installed programs
Review your device’s list of installed programs for anything you don’t recognize. If you find something suspicious, uninstall it. Mobile users should review their list of installed apps. Android and iOS both allow users to view lists of apps filtered by the permissions they have, which is useful if you think you may have a Trojan. Look for suspicious apps with potentially dangerous permissions like SMS/call access, location services, accessibility services, and administrator privileges.
Whichever device you use, try to manually uninstall any app or program that you’ve identified as suspicious. You may need extra tools to eliminate the threat, but basic Trojans can be dealt with simply by uninstalling them.
Monitoring network activity
Keeping an eye on your network traffic can help detect Trojans and other malware. Unusual spikes in data usage, connections to unfamiliar IP addresses, or unexpected outgoing traffic may indicate that a Trojan is sending information from your device or communicating with a remote server.
You can monitor network activity using built-in tools like Resource Monitor on Windows and the Network tab of Activity Monitor on Mac, both of which can be accessed through a simple device search.
Look out for processes consuming unusually high bandwidth or establishing frequent external connections. Regularly reviewing network activity can alert you to hidden threats that might otherwise go unnoticed.
Prevention strategies against Trojans
Trojans rely on deception and can execute a wide variety of attacks. To stay safe, it’s best to know the common strategies cybercriminals use and the places where Trojans are commonly distributed, protect yourself with security software, and adopt practices that reduce your level of risk.
Best cybersecurity practices
To best insulate yourself against Trojans and other threats, there are a few practices you should adopt.
Keeping software up-to-date
Regularly updating your device’s OS and all of your programs is a vital cybersecurity practice that will make you less vulnerable to Trojans and other threats. Cybercriminals often exploit vulnerabilities in outdated software to deliver malware, so keeping everything current closes these security gaps. From your OS to your browser, antivirus, and virtual private network (VPN), install updates whenever they become available.
Using strong passwords
A keylogger Trojan can crack even the strongest of logins, but using strong passwords is an important step for protecting all of your accounts. Credentials should be long and contain a mix of numbers, letters, and symbols. Using random strings of characters is a great strategy for password security, and a password generator can help create complex, secure passwords for all your accounts.
For added convenience and security, a password manager like ExpressKeys can securely generate, store, and autofill complex passwords across your devices. This reduces the risk of reusing passwords or exposing them to malware.
It’s also best to combine strong passwords with two-factor authentication (2FA). Doing so means that even if a Trojan compromises one of your passwords, attackers still face another barrier before they can access your accounts.
Safe browsing habits
Since Trojans are primarily spread online, you should take particular care while browsing.
Avoiding phishing emails
Practicing caution with email is critical. Always double- or triple-check the sender’s address before opening attachments or clicking links, and verify unexpected emails from contacts through alternate channels, such as a phone call. Being able to recognize phishing attempts is an important skill for any internet user.
Identifying malicious links
Avoid visiting malicious websites, stay away from freeware providers, and be very cautious if you intend to torrent files. ExpressVPN users can take advantage of its advanced protection tools to add further defenses against a variety of web-based threats. Features vary across plans, but ExpressVPN can block ads, dangerous domains, and more.
Cybersecurity awareness training
Businesses that handle sensitive data may want to consider investing in cybersecurity awareness training. This can provide up-to-date knowledge of current threats, teach strategies to identify suspicious activity, and reinforce habits that minimize the likelihood of Trojan infections.
Real-world examples of Trojan attacks
Unlike the mythical wooden horse, computer Trojans are a real-world threat that affects individual users, large corporations, and governments. The table below highlights key details of several notable Trojan attacks.
| Year | Trojan | Primary Target | Threat executed | Impact |
| 1989 | AIDS Information | Computer files | Ransomware | Demanded $189 per victim via mail to unlock |
| 2007 | Zeus (also known as Zbot) | Financial information | Keylogger, form grabber, web injection, botnet | Malware-as-a-Service (MaaS) model; variants like GameOver Zeus caused estimated losses over $100 million |
| 2007 | Qakbot (also known as Qbot or Pinkslipbot) | Financial information | Keylogger, email harvester, botnet, ransomware, and more | Active for over a decade, up to €54 million in ransoms were paid |
| 2013 | CryptoLocker | Computer files | Ransomware | One of the first high-profile ransomware outbreaks, estimated ransoms paid over $27 million |
| 2014 | Dyre (or Dyreza or Dyranges) | Financial information | Keylogger and browser injections | Corporate banking malware; global losses estimated in billions |
| 2016 | Triada | Financial information | Backdoor access, crypto clipper | Over $264,000 in crypto; remains a threat |
| 2022 | ANOM | Criminal suspects | Honeypot | 500+ worldwide arrests by law enforcement agencies |
FAQ: Common questions about Trojans
What does a Trojan virus do?
Trojans aren’t viruses but rather a distinct type of malware that uses deception to infiltrate devices by masquerading as legitimate software or files. Once installed, these programs can execute a variety of attacks depending on the nature of the specific Trojan. Possible outcomes include the theft of your personal information, long-term surveillance, your files being held for ransom, and your device being hijacked to mine crypto or operate in a botnet.
How do I know if I have a Trojan on my device?
Detecting a Trojan requires scanning your device with current, reputable antimalware software. You may be able to identify one manually, but this is not always efficient or possible. Antivirus software, on the other hand, examines system directories and processes to identify malicious code and unauthorized programs.
How can I remove a Trojan permanently?
You can often remove a Trojan permanently by using up-to-date antivirus software. As a last resort, you may want to consider performing a factory reset of your device to get rid of Trojans, but you will lose all your data and risk reinstalling infected files from backup.
What are the consequences of a Trojan infection?
Trojan infections can lead to a number of negative effects, depending on the nature of the specific threat. These include sensitive data leaks, financial losses, and identity theft. Trojans also put your computer under an attacker’s control, such as for use in a botnet to deploy distributed denial of service (DDoS) attacks.
Can Trojan viruses infect mobile devices?
Trojans can infect mobile devices like iOS and Android smartphones. Trojans for mobile devices are more prevalent on Android, with iOS devices better insulated due to the “walled garden” nature of the Apple ecosystem. That said, apps that misrepresent their true purpose may potentially be found on both Apple’s App Store and the Google Play Store.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN