What is IIoT and why its security matters more than ever

In modern industry and operations, more devices than ever are connected to networks and each other through the Industrial Internet of Things (IIoT). This connectivity allows factories, plants, utilities, and other systems to operate smarter using machine-to-machine communication and real-time analytics. It helps optimize production, reduce downtime, enable predictive maintenance, and improve decision-making and resource management.
However, every new connection also increases risk for critical infrastructure. Each sensor or device can become an entry point for cyberattackers, putting operations, schedules, and even public and worker safety at risk. Because many IIoT devices lack strong security features, they’re easier for attackers to target if not properly protected. That’s why securing IIoT is more important than ever.
In this article, we’ll explore what IIoT is, why its security is essential, how virtual private networks (VPNs) can help, and the best practices organizations should adopt to stay ahead of evolving threats.
Understanding IIoT in simple terms
Here’s a quick rundown of what IIoT is, how it works, and what makes it different from the Internet of Things (IoT).
What is the Industrial Internet of Things (IIoT)?
The Industrial Internet of Things (IIoT) is a network of connected sensors, devices, and machines used in industrial environments. These systems collect and share data to enhance productivity, safety, and reliability.
IIoT connects operational technology (OT), such as machinery and control systems, with information technology (IT) that processes and analyzes data. This integration enables real-time monitoring, predictive maintenance, process automation, and data-driven decision-making.
Data from sensors and machines is sent to central systems, such as cloud platforms, where advanced analytics identify patterns, predict potential issues, and recommend improvements. Some data is processed locally at the equipment level to support faster, on-site decisions.
Unlike consumer IoT applications that use data to personalize experiences, such as how apps and online services collect information about people to personalize ads, suggest products, or track habits, a concept known as the Internet of Behaviors (IoB), IIoT focuses on optimizing industrial operations and asset performance.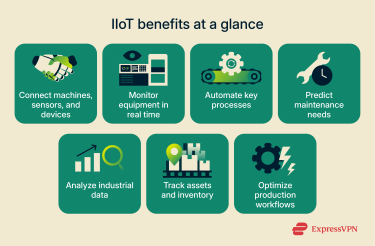
How IIoT differs from traditional IoT
The IIoT and the Internet of Things (IoT) share the same basic idea: connecting devices and enabling them to share data. However, they differ in purpose, environment, and requirements.
IoT involves everyday consumer devices, such as smart thermostats, wearable fitness trackers, and home assistants. These devices help people automate tasks, monitor their personal environment, and make data-driven choices in daily life, improving convenience, comfort, and efficiency in everyday routines.
IIoT applies the same concept to industrial settings, such as factories, power plants, farms, and logistics centers. Unlike consumer IoT devices, which can tolerate minor errors or delays, IIoT systems support critical industrial processes. Therefore, they require stricter security, fast and reliable communication, and seamless integration with the machines and equipment they control to ensure efficiency, safety, and continuous operation.
Real-world examples of IIoT in action
IIoT is already transforming industries around the world. Here are some current applications of IIoT:
- Manufacturing: Sensors on machinery, assembly-line monitors, and automated quality-control systems help track machine performance, monitor production rates, and detect defects. They can also alert staff to potential problems or wear on equipment so repairs can be made before machines break down.
- Transportation: IIoT tracks vehicles, monitors fuel usage, and optimizes delivery routes. It can also detect maintenance issues early and monitor driver behavior and traffic conditions to improve safety and reduce downtime.
- Agriculture: Soil sensors, weather monitors, and automated irrigation systems collect data on moisture, nutrients, and crop health. Farmers can use this information to adjust watering and fertilization schedules, plan harvesting, and reduce waste, making crop production more efficient and sustainable.
- Construction: Smart sensors track equipment usage, environmental conditions (such as curing times and weather), and the location of tools and machinery. This helps project managers optimize equipment allocation, reduce material loss, and improve safety on‑site.
- Energy/Utilities: IIoT systems monitor infrastructure like power grids, transformers, pipelines, and wind turbines. Sensors can detect equipment wear, measure energy flow, and track system performance, allowing operators to respond quickly to issues, optimize distribution, and schedule maintenance to prevent breakdowns.
- Healthcare: IIoT devices in hospitals and clinics monitor patient vital signs, allowing staff to respond quickly to any changes. They also track the location and status of critical equipment, ensuring devices are available when needed and properly maintained. Additionally, it can also monitor temperature and humidity in sensitive areas, like operating rooms and equipment storage areas, to help maintain safety and prevent infections.
Why IIoT needs stronger security
IIoT systems control vital operational and industrial processes, from factory production lines to water treatment and healthcare systems, and attacks targeting them are increasing. A recent report by multinational cybersecurity firm Palo Alto Networks & Starfleet showed that nearly four out of five security leaders said their organization had faced an IIoT-focused attack in the past year. For these reasons, it’s essential that organizations take proactive measures to protect their operations.
In the following sections, we’ll explore what makes industrial devices vulnerable to attacks, what can happen if systems are compromised, and the common threats targeting IIoT networks.
How industrial devices are vulnerable to attacks
Industrial devices face several vulnerabilities that make securing them challenging.
Many IIoT devices simply aren't designed with security in mind; most IIoT traffic is unencrypted, meaning anyone who intercepts it can view the data and potentially manipulate device behavior.
Legacy equipment compounds the problem. Many industrial networks still rely on older systems not built for secure internet connectivity, and updating or patching them can be difficult without disrupting operations.
IIoT systems also create more opportunities for cyberattacks compared to traditional industrial systems, as they rely on wireless connections, cloud platforms, and third-party software, each of which can serve as a potential entry point for attackers. In contrast, traditional setups were typically isolated, with closed internal networks and far fewer connections for attackers to exploit.
Additionally, managing IIoT devices is complex; many organizations lack full visibility into their IIoT devices and network activity, meaning they don’t always know which devices are connected, what data is being transmitted, or when something unusual occurs. This makes it harder to detect vulnerabilities or respond quickly to security incidents.
Furthermore, some networks lack proper network segmentation, or separation between systems. This means that if a bad actor gains access to one device, they may be able to reach others on the same network, allowing the attack to spread rapidly.
Finally, the use of default passwords or the absence of authentication controls, such as multi-factor authentication (MFA), increases the risk of unauthorized access.
What happens when IIoT systems get hacked?
Because IIoT systems interact directly with physical processes, a security breach can cause more than just data loss. When software controls machinery, digital risk also means physical risk.
Safety hazards
Because IIoT systems directly control physical processes, safety is the most critical concern. A security breach in these environments can lead to real-world harm, from severe injuries to loss of life, not just data compromise.
In industrial settings, safety standards exist because failures can cost lives. And when cybersecurity is weak, those hazards can re-emerge through software failure.
For example, a compromised industrial robot could move unpredictably on a factory floor, a tampered furnace controller could exceed safe temperature limits, or a disrupted chemical-handling system could trigger an explosion, toxic exposure, or fire affecting both on-site personnel and surrounding communities.
Disruption to operations and equipment
An IIoT hack can damage machinery or force it offline, which may necessitate costly repairs and cause delays or stoppages to production lines. This can impact not only routine manufacturing operations but also critical infrastructure and essential services. IIoT solutions in public safety, for example, rely on secure and reliable device operation to monitor traffic, environmental conditions, or emergency alerts.
Financial losses
Downtime, wasted materials, and emergency interventions increase costs. According to IBM's Cost of a Data Breach Report 2025, the average cost of a breach is $4.44 million, and this number climbs to $7.42 million for breaches in the healthcare sector.
Supply chain impact
Production delays can spread through suppliers, warehouses, and distributors, leading to shortages or stopping assembly lines. For example, a problem at a food plant could slow store deliveries, while a disrupted automotive factory could halt car production.
Common threats to IIoT networks
IIoT networks face a variety of threats that exploit the vulnerabilities in devices, systems, and implementations. Some of the most common threats include:
- Brute-force attacks: Brute-force attacks use automated tools to try thousands of login combinations until attackers gain access.
- Credential stuffing: Credential stuffing is when attackers try username/password pairs stolen from other breaches on IIoT devices and services; this works because people often reuse passwords across different platforms.
- Botnets: Compromised IIoT devices can be co-opted into botnets, which are networks of infected devices controlled by attackers to launch large-scale attacks, spread malware, or disrupt operations.
- Ransomware: Ransomware is a type of malware that encrypts system data or locks users out of critical industrial controls until a ransom is paid.
- Firmware/software exploits: Attackers exploit vulnerabilities in outdated or unpatched IIoT device firmware or software to gain unauthorized access, execute malicious code, or disrupt operations.
- Denial-of-service (DoS) attacks: DoS attacks aim to overload a system, server, or network with traffic or requests to render them slow or unresponsive.
- Man-in-the-middle (MITM) attacks: An MITM attack occurs when a threat actor secretly intercepts and possibly alters communications between two legitimate parties (e.g., an IIoT sensor and its central control server). This allows the attacker to eavesdrop on data, inject false commands, or manipulate readings.
- Supply chain attacks: Threat actors compromise IIoT hardware or software components during manufacturing, distribution, or updates, potentially affecting many devices at once and creating widespread operational risks.
- Physical tampering: IIoT devices placed in remote or unsecured locations can be physically accessed, allowing attackers to extract data, install malicious hardware/firmware, or replace sensors, bypassing network controls entirely.
Can VPNs protect industrial systems?
Yes. VPNs are often used to secure remote access to IIoT devices and networks. The following sections examine how they work and what advantages they offer compared with open industrial networks.
How a virtual private network (VPN) secures remote IIoT access
In an industrial environment, remote connections allow operators to monitor and control equipment scattered across multiple sites. But because many IIoT devices connect over public or cellular networks, those links can be easily intercepted or tampered with if left unsecured.
A good VPN for IIoT maintains reliable IIoT connectivity while protecting data from unauthorized access by creating an encrypted, private channel for communication between remote devices, gateways, and control systems.
Through that encrypted tunnel, data moves safely from the field device to the enterprise network or cloud platform without ever appearing on the open internet. Each device authenticates before joining the VPN, ensuring that only approved users or endpoints can exchange information. This prevents outsiders from issuing commands or viewing sensitive operational data.
VPNs can also limit how much of the IIoT network is visible and accessible to potential attackers. They can remove the need for devices to use public IP addresses by routing traffic through private gateways rather than the general internet. While some older or cloud-dependent systems may still require external access, this still represents a significant security improvement.
Encrypted tunnels vs. open industrial networks
Many industrial systems still communicate over unencrypted networks, whether on a company’s internal network or the public internet. In these “open” environments, data can be intercepted, altered, or monitored as it travels between devices. Devices in these environments are also easier for attackers to discover and target.
VPNs address these risks by creating encrypted tunnels between industrial devices and the enterprise or cloud systems they rely on. These tunnels protect data end-to-end, so even if traffic is intercepted, it can’t be read or modified. Securing communications in this way prevents eavesdropping, blocks unauthorized commands, and limits the ways attackers can access critical systems compared with unprotected networks.
| Feature / Risk | Open industrial networks | Encrypted VPN tunnel |
| Data encryption | None or minimal | Encrypted end-to-end |
| Exposure to public networks | High | Reduced |
| Vulnerability to interception | High | Low |
| Risk of unauthorized commands | High | Low |
Benefits of VPNs for IIoT infrastructure
VPNs offer several key benefits for strengthening IIoT infrastructure:
- Encrypted communications: VPNs secure data transmitted between devices and enterprise or cloud systems, keeping it safe from interception or tampering even over public or cellular networks.
- Reduced exposure to attackers: By keeping devices off the public internet and routing traffic through private tunnels, VPNs limit opportunities for unauthorized access or exploitation.
- Secured remote access: Operators can safely monitor, manage, and update devices from anywhere without exposing systems to external threats.
- Improved regulatory compliance: VPNs help organizations meet data-protection and privacy standards by encrypting traffic and restricting device exposure.
- Centralized management and monitoring: Advanced VPN solutions allow administrators to enforce access controls, monitor traffic, and detect irregularities in real time, supporting scalable and secure IIoT deployments.
Best practices to keep IIoT secure
 Effective IIoT cybersecurity requires a combination of technical safeguards, operational procedures, and proactive management. In the following sections, we’ll explore key strategies for protecting IIoT devices and networks.
Effective IIoT cybersecurity requires a combination of technical safeguards, operational procedures, and proactive management. In the following sections, we’ll explore key strategies for protecting IIoT devices and networks.
Use encrypted connections for remote control
Remote access is a key part of modern IIoT operations, allowing operators to monitor equipment, perform maintenance, and adjust settings from anywhere.
Encrypting these connections with a VPN ensures that data traveling between devices, gateways, and control systems remains confidential and protected from tampering. Strong authentication mechanisms, such as multi-factor authentication (MFA) or single sign-on (SSO), further reduce the risk of unauthorized access while maintaining operational efficiency.
Segment your networks to limit risk
Network segmentation divides an IIoT environment into smaller, isolated sections, preventing a breach in one area from spreading across the entire system. By separating devices, control systems, and administrative networks, organizations can restrict access to sensitive resources and limit the impact of cyberattacks.
This segmentation is key to preventing lateral movement by attackers. Even if one device or segment is compromised, strict boundaries and access controls stop attackers from easily moving through the network to access other critical systems. Limiting lateral movement not only reduces risk but also makes containment and response more manageable.
Proper segmentation also simplifies monitoring, allowing administrators to detect irregular activity more quickly and apply targeted security controls to each segment. This approach helps maintain operational continuity, especially in complex industrial networks.
Keep devices and firmware up to date
Many IIoT devices have limited built-in security, and vulnerabilities in outdated firmware can be exploited by attackers. Regularly updating device firmware and software ensures that known security flaws are patched, access controls are up to date, and new protective features are enabled. Maintaining an update schedule and leveraging centralized management tools help operators stay ahead of emerging threats while minimizing disruption to critical operations.
However, in many industrial environments, updating firmware is not always straightforward or even possible. Legacy hardware may be highly customized, niche, or from manufacturers that no longer support the device or exist at all. In such cases, replacing or upgrading hardware may be cost-prohibitive, risky, or operationally infeasible.
When firmware updates are unavailable, organizations must adopt a threat-modeling approach to understand and prioritize risks posed by unsupported devices. This includes:
- Assessing the criticality of the device and potential impact of compromise.
- Evaluating the feasibility and cost of hardware replacement or mitigation.
- Minimizing the device’s attack surface through the other solutions mentioned on this list.
Apply strict access control
Controlling who or what can access IIoT devices and data is essential for security. To achieve this, organizations can adopt a zero-trust approach, which assumes that no user or device is inherently safe, requires every access attempt to be verified, and applies the principle of least privilege by giving each user or device only the access they need.
Monitor IIoT devices and networks continuously
Keep an eye on IIoT devices and network traffic to spot unusual behavior, such as unexpected commands or unfamiliar devices. Early detection helps organizations respond quickly to potential threats.
Set up physical security controls
Even the most secure IIoT networks are vulnerable if devices can be physically accessed by attackers. Locking enclosures, controlling access to equipment rooms, using CCTV monitoring, and installing environmental sensors can help prevent tampering, theft, or sabotage.
FAQ: Common questions about IIoT
Can a VPN protect smart factories?
Yes, a VPN can help protect smart factories by encrypting communications between Industrial Internet of Things (IIoT) devices, gateways, and control systems. This prevents unauthorized access, eavesdropping, and tampering with sensitive operational data, even over public or cellular networks. Advanced VPN setups can also allow secure direct connections between devices and centralized management with strong authentication, minimizing the risk of cyberattacks.
Is IIoT a threat to user privacy?
Unlike Internt of Things (IoT) devices, which often collect personal data such as usage habits or health metrics, Industrial Internet of Things (IIoT) devices are primarily used in industrial settings. But that doesn’t mean they can’t affect user privacy. Industries like healthcare, utilities, or transportation may handle data linked to individuals, and a breach could expose sensitive user information. That’s why it’s important to implement strong security measures, including encryption, access controls, and network segmentation.
What kind of data do IIoT devices collect?
Industrial Internet of Things (IIoT) devices collect real-time operational data, including machine performance, production metrics, energy usage, equipment location, and environmental conditions. This data enables predictive maintenance, process optimization, and supply chain coordination, helping organizations improve efficiency and reduce downtime. The sensitive nature of this information makes robust security measures essential to prevent interception or misuse.
What are the biggest IIoT security risks today?
The main Industrial Internet of Things (IIoT) security risks include unencrypted communications, default passwords, outdated firmware, network exposure, and potential insider threats. Threats like ransomware, botnets, man-in-the-middle (MITM) attacks, and supply chain compromises exploit these vulnerabilities, resulting in serious safety hazards, operational disruption, equipment damage, and financial loss if devices and networks aren’t properly secured.
How do companies secure industrial networks?
Companies secure industrial networks by using encrypted connections (such as VPNs) for remote access, segmenting networks to isolate critical systems, and keeping devices and firmware up to date. These practices reduce attack surfaces, prevent lateral movement by attackers, and allow centralized monitoring to detect irregular activity. Combining technical safeguards with operational procedures creates a layered defense against evolving threats.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN