-

How to work from home: Keeping safe and sane while remote
The coronavirus outbreak has prompted a lot of companies, including Google and Apple, to recommend their employees work from home. Many events have been canceled, and flights to many countries now inc...
-

Let’s Encrypt has issued a billion certificates, securely encrypting nearly 200 million sites
An effortless way to check whether the site you just logged on to maintains an encrypted connection is whether it starts with HTTP or HTTPS. HTTPS (Hyper Text Transfer Protocol Secure) encrypts the co...
-

The uncrackable Android trojan: What is xHelper?
We’ve advised our readers to stay safe from malware and trojans by keeping their devices updated at all times, but a new strain caught in the wild is seemingly impenetrable to every cybersecurity be...
-

4 new cybersecurity threats in 2019
Cybersecurity threats continue to evolve, and the nature and sophistication of attacks vary widely. With more businesses moving their files to the cloud, health care organizations shifting to electron...
-
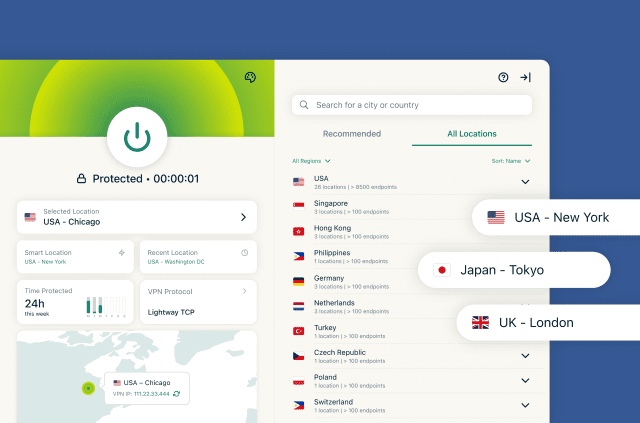
Why you can't judge a VPN by its server count
When it comes to choosing a VPN company, there are many things you'll want to take into account, such as do they provide good speeds? Do they have apps for all my devices? And are they well known and ...
-

What is a Bitcoin node and who needs one?
The Bitcoin network does not have a central authority that decides which transactions are valid and which are not. There is nobody who issues coins, and nobody who can take them back. Nobody knows how...
-
11 massive government data breaches
We’re constantly hearing about data breaches lately—and it’s no wonder, given that billions of personal records are exposed every year. While the majority of cybersecurity headlines center ar...
-

9 things you can do with a home server
Running your own server at home can be cheap and requires only basic knowledge of the command line. An old laptop can be converted into a server without any physical modifications, and even a modest d...
-

Why should I use two-factor authentication?
You might have skipped over your email provider’s prompt: Turn on two-factor authentication. Two-factor authentication, or 2FA, is a secondary security measure for logging into an online account, wh...
-

Why you shouldn’t ignore ‘Update Your Device’ messages
It’s pretty much second nature at this point. We start our laptops and hunker down in our seats, ready to power through the day with a steaming cup of coffee. As we browse through our daily calendar...
Tips & tricks





