What is an IP reputation attack? Learn how to prevent it
Many public IP addresses have a reputation that different online services use to decide whether traffic should be treated as legitimate or suspicious.
An IP reputation attack targets that score. This article explains what IP reputation attacks are, how they work, how to recognize the signs early, and the steps to take to recover and reduce the risk of future damage.
What is an IP reputation attack?
An IP reputation attack is a deliberate attempt to get an IP address flagged as suspicious by services that rely on reputation signals to stop abuse. A damaged IP reputation can lead to blocking, throttling, or service denial across email platforms, websites, APIs, and networks.
Who assigns IP reputation scores?
There’s no universal IP reputation score and no single authority that assigns reputation to IP addresses. Reputation data is produced by a combination of reputation data providers and individual services.
Reputation data providers specialize in collecting abuse signals, and they publish IP reputation data for others to consume, often in the form of blocklists or reputation feeds that aggregate reports of spam, scanning, and other abusive activity.
At the same time, internet-facing services that rely on IP reputation scores also directly observe traffic themselves and create their own internal reputation scores, using models tailored to their specific abuse and risk profiles.
Who uses IP reputation data?
IP reputation data, whether sourced internally or from third parties, is used by a wide range of internet-facing services, including:
- Email service providers to filter spam and phishing.
- Content delivery networks (CDNs) and distributed denial-of-service (DDoS) protection providers to block or challenge risky traffic.
- Web application firewalls (WAFs) and bot detection tools to stop scraping, credential stuffing, and automation.
- Fraud and login protection systems to detect suspicious sign-ins and transactions.
- API platforms to rate-limit or block abusive request patterns.
How IP reputation scores work
Most IP reputation systems work the same way at a high level: they evaluate past and current behavior from an IP address. They typically look at traffic volume, consistency, error rates, complaint reports, and associations with known malicious activity.
The difference is that each platform builds reputation independently, using its own data sources and scoring logic. That reputation is then used to make automated decisions about how traffic should be handled, such as allowing requests normally, applying rate limits, requiring additional verification, or blocking traffic entirely.
Because these systems operate independently, there is no single scale or shared definition of “good” or “bad” reputation. An IP address may be considered trustworthy by one service and suspicious by another at the same time. Reputation is also expressed in different ways: some services assign a numeric score, while others classify IPs into broader risk categories.
It’s also important to note that IP reputation isn’t always measured at the single-IP level. Many systems apply reputation to IP ranges or even an entire hosting provider’s network. That’s why shared infrastructure, such as shared hosting, Network Address Translation (NAT) networks, or reused cloud IPs, can sometimes get flagged even when a specific business isn’t doing anything wrong.
What makes an IP address trustworthy or risky
IP reputation systems evaluate both behavioral signals and infrastructure context to assess risk.
Behavioral signals reflect how traffic from an IP behaves over time. IPs with consistent request patterns, low error rates, and no association with spam, malware, or phishing tend to accumulate a positive reputation. In contrast, sudden traffic spikes, repeated failed requests, automated or bot-like activity, and abuse-related indicators are commonly associated with low reputation.
Beyond behavior, reputation systems also consider the infrastructure context around an IP, including:
- Residential vs. datacenter IPs: Traffic from cloud and hosting ranges is more often associated with automation and abuse than traffic from residential networks.
- Shared vs. dedicated IPs: Shared IPs can inherit risk from other tenants, while dedicated IPs used consistently by a single party tend to build a more stable reputation over time.
- IP history and reassignment: IPs previously associated with abuse may retain elevated risk even after being reassigned to a new owner.
- Network-level reputation: Some systems evaluate reputation at the subnet or network level, not just for individual IPs.
Integrating behavior and infrastructure signals gives services a more comprehensive understanding of an IP’s risk profile. Reliable addresses tend to show consistent, predictable behavior and exist in infrastructure environments that aren’t closely linked to misuse.
How do IP reputation attacks work?
IP reputation attacks manipulate the signals that reputation systems use to assess risk, causing normal traffic to resemble patterns typically associated with abuse. To do that, they can use a range of techniques, including: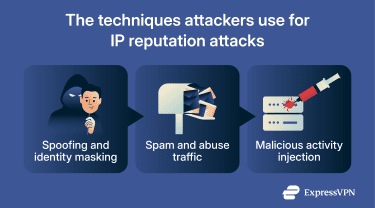
Spoofing and identity masking
In spoofing and identity masking attacks, attackers make it appear as though abusive activity is originating from the victim’s IP address. They do this either by forging source IP information in network traffic through IP spoofing or masking their identity behind intermediary systems that are closely associated with the user’s IP space.
IP spoofing involves falsifying the source IP address on outgoing traffic so it appears to come from another system. Although possible, in practice, this technique has limited effectiveness because most modern services require a two-way connection: responses are sent back to the claimed source IP, not to the attacker. As a result, spoofed traffic typically can’t complete normal requests or trigger higher-level abuse detection on its own.
Because of these limitations, attackers more often rely on identity masking, where they route traffic through intermediary systems, such as open proxies, misconfigured NAT gateways, or compromised hosts, that can complete real connections. Since the traffic legitimately passes through these systems, reputation services associate the abusive activity with IP addresses linked to the victim.
Spam and abuse traffic
In spam and abuse traffic attacks, attackers generate large volumes of low-quality or abusive traffic that legitimately originates from the victim’s IP address.
This usually happens by abusing systems the victim owns or shares, such as compromised email accounts, exposed APIs, contact forms, signup flows, or other outward-facing endpoints. From the perspective of receiving services, the traffic is valid at the network level because it truly comes from the victim’s IP, even if the content or behavior is abusive.
Because the activity matches well-known abuse patterns, such as high-volume sending, automated submissions, or repeated failed interactions, reputation systems associate the behavior with the victim’s IP and degrade its reputation. In some cases, even short bursts of this traffic can be enough to trigger automated penalties.
Malicious activity injection (botnets, brute force, etc.)
In malicious activity injection attacks, attackers deliberately generate traffic patterns that make it appear as if the IP is actively attacking systems.
This can include brute-force login attempts, credential-stuffing campaigns, automated scanning, or botnet-style probing directed from or through the victim’s IP address. Even when these attempts fail or don’t result in a compromise, they create indicators of malicious intent. And because these patterns are closely tied to real attacks, reputation systems may respond aggressively.
How bad IP reputation affects your business
A damaged IP reputation doesn’t just cause technical inconvenience. Reputation systems sit between your infrastructure and external services, so problems at this layer can disrupt communication, operations, and trust across the business.
Loss of communication with clients
Poor IP reputation has the potential to disrupt outbound communication across multiple channels. External services may block, delay, or filter traffic from low-reputation IPs, which can prevent messages from reaching clients, partners, or vendors and cause exchanges to stall without warning.
IP reputation-based filtering could also interrupt application-driven communication. Platforms can reject or throttle API calls, authentication requests, and system notifications, which breaks logins, confirmations, and transactional messaging that clients rely on.
Legal and compliance implications
IP reputation damage may create compliance risks in industries that rely on the timely delivery of notices, confirmations, or records. If messages fail to reach recipients, organizations may face consequences even when the underlying cause is external filtering.
In regulated environments, IP reputation-related disruptions can also affect audit trails, incident notifications, and even required disclosures, as third-party blocking can make it difficult to demonstrate that communications were sent but not received.
Impact on brand trust and revenue
Persistent reliability issues shape how customers perceive a service. When messages fail to arrive, systems block access, or services behave unpredictably, customers attribute the failure to the business.
Over time, these failures can drive churn, increase abandoned transactions, and reduce engagement. For customer-facing services, even brief disruptions might reduce conversion rates and long-term revenue.
How to know if you’re under attack
IP reputation attacks can be hard to spot because nothing “breaks” in an obvious way. The fastest way to confirm something is wrong is to look for patterns across multiple systems at the same time.
Common indicators of IP reputation issues
Some of the most common signs that an IP reputation problem is developing include:
- Unexpected spikes in HTTP errors from services that normally behave reliably.
- CAPTCHA loops or repeated verification prompts during logins or form submissions.
- Sudden drops in traffic or conversions without an obvious technical cause.
- Third-party request failures, such as blocked API calls, failed webhooks, or rejected integrations.
- Security alerts showing repeated failed authentication attempts or scanning activity.
- User reports of access issues, often limited to specific regions, networks, or providers.
Note that some of these indicators have many possible causes and might not be directly related to malicious activity.
Email deliverability and bounce rates
Email is often the first place where reputation issues become visible, because major providers aggressively filter based on IP and domain signals. You should watch for:
- Increased bounce rates, especially “blocked” or “rejected” messages.
- Messages landing in spam that previously went to inbox.
- Delivery delays (messages arriving hours later).
- Warnings from providers about suspicious sending behavior.
- Sudden drops in open rates without changes to content or audience.
If your sending volume hasn’t changed but deliverability suddenly gets worse, that could be an indicator that your IP reputation is under pressure.
IP blocklist monitoring tools
Blocklists aren’t the only reputation signal, but they’re one of the clearest external indicators that an IP is being treated as risky. A practical workflow is:
- Check whether your IP appears on major blocklists.
- Identify which IP is affected (outbound mail IP vs web server IP vs NAT gateway IP).
- Review recent logs for spam, brute-force attempts, or unexpected outbound traffic.
- Fix the underlying issue before requesting delisting.
If you’re on shared infrastructure, you’ll also want to confirm whether the listed IP is truly dedicated to you or part of a shared pool.
Popular IP blacklist checkers
Checking reputable blocklists is one of the fastest ways to confirm if an IP has been flagged by external filtering systems. Commonly trusted IP blacklist checkers include:
- Spamhaus: One of the most widely used sources for IP reputation data, particularly for spam and malware-related abuse.
- Spamcop: Useful for identifying recent spam complaints linked to IPs.
- MxToolbox: Aggregates results from multiple blocklists in a single lookup.
Email authentication and DNS tools
If email deliverability is part of the issue, reputation checks should be paired with email authentication and Domain Name System (DNS) validation. Even a clean IP can struggle if authentication is missing or misconfigured. Useful tools include:
- Google Workspace: Admin Toolbox provides diagnostic tools that let domain administrators check email authentication alignment and see how Gmail evaluates a domain’s sending reputation and configuration.
- MailTester: Evaluates authentication, spam filtering signals, and reputation-related indicators.
- DNSChecker: A public lookup tool that lets you verify whether DNS and reverse DNS records are resolving quickly across different global regions.
How to respond to an IP reputation attack
Once you suspect an IP reputation issue, the goal is to stop the damage, confirm what’s affected, and restore service as quickly as possible.
Steps to remove your IP from blacklists
If your IP has been blocklisted, the fastest way to recover is to treat it like a two-part problem: fix what triggered the listing, then work through the delisting process. Most blacklists won’t keep you listed forever, but if you request removal before the root cause is resolved, you’ll often end up right back where you started. Here’s a practical step-by-step approach:
- Confirm which IP is actually listed: Many organizations have multiple public IPs (for web, outbound email, and NAT gateway). Start from the symptom and identify the IP that external services are seeing.
- Identify the blacklist(s) and the reason for listing: Use a blacklist checker, then confirm directly with the blocklist operator. Some lists provide a reason, which helps you narrow the root cause.
- Fix the underlying cause before requesting removal: This typically means securing compromised email accounts, closing misconfigured mail relays, removing malware or unauthorized outbound traffic, or addressing abusive automation on shared infrastructure. Requesting delisting before the behavior is resolved usually results in rapid relisting.
- Follow the delisting process (or wait for auto-expiration): Some blacklists expire automatically after a cooldown period. Others require a removal request and proof that the issue is resolved.
- Monitor for relisting: If the IP gets listed again quickly, assume the underlying behavior is still happening, or the IP is shared and the abuse isn’t coming from you.
How to recover email deliverability
Getting delisted is only part of the fix. Even after your IP is removed from a blacklist, email providers may continue filtering your messages until they see consistent, legitimate sending behavior again.
- Verify your authentication records: Make sure your authentication records are correct and aligned with the domain you’re sending from. This won’t instantly restore reputation, but it helps providers validate that your mail is legitimate while rebuilding trust.
- Prioritize critical email traffic: If you send both marketing and transactional email, protect the important messages first (password resets, receipts, account alerts). If possible, separate them so a marketing spike doesn’t damage your core deliverability.
- Ramp volume back up gradually: A sudden spike can look like a repeat incident. Start small, monitor results, then increase volume in stages.
- Watch provider-specific signals: Track bounced messages and spam placement by mailbox provider. Gmail, Microsoft, and Yahoo can respond differently to the same sending IP, so a recovery may look “fixed” in one place and broken in another.
- Consider switching IPs only if it’s truly necessary: Moving to a fresh sending IP can help in severe cases, but it only works if the underlying cause is gone. Otherwise, the new IP will get flagged, too.
Timeline for reputation recovery
There isn’t a universal recovery timeline because every provider scores reputation differently and the severity of the incident matters. The biggest factor is consistency. Reputation improves when systems see a stable return to normal behavior over time, without repeated spikes, complaints, or security triggers.
Strategies to reduce the risk of IP reputation attacks
Preventing IP reputation attacks means reducing the signals that automated systems associate with abuse while simultaneously limiting opportunities for attackers to misuse your infrastructure.
Best practices for secure email sending
Consistent, predictable sending behavior is one of the strongest defenses against reputation damage. Additional best practices include:
- Scaling traffic gradually instead of sudden sending spikes.
- Avoiding burst sending patterns that resemble automation.
- Maintaining clean recipient lists and removing invalid addresses.
- Monitoring bounce rates and spam complaints closely.
- Using clear opt-in practices to reduce unsolicited traffic signals.
Technical measures (SPF, DKIM, DMARC, rDNS)
These controls don’t stop abuse by themselves, but they help receiving systems correctly attribute traffic, so malicious activity is less likely to be misattributed to your IP. Key controls include:
- Sender Policy Framework (SPF): Declares which servers are allowed to send email on behalf of your domain, reducing the risk of unauthorized sending being attributed to you.
- DomainKeys Identified Mail (DKIM): Adds a cryptographic signature to outgoing messages so receivers can verify the message wasn’t altered and actually came from your domain.
- Domain-based Message Authentication, Reporting, and Conformance (DMARC): Tells receiving systems how to handle messages that fail SPF or DKIM checks, helping prevent spoofed or abusive traffic from damaging your reputation.
- Reverse DNS (rDNS): Maps a sending IP address back to a domain name, which many providers use as a basic trust and consistency signal.
- Authentication alignment: Ensures SPF, DKIM, and DMARC all match your actual sending behavior, avoiding mixed or conflicting signals that can hurt reputation.
Staff education and social engineering awareness
Human error is a common entry point for reputation damage. Compromised credentials, phishing attacks, or unauthorized automation could generate traffic patterns that resemble abuse.
Training staff to recognize social engineering attempts and enforcing strong access controls reduces the risk that an attacker can misuse legitimate systems. Clear internal processes for reporting suspicious activity also help contain issues before they escalate into reputation problems.
FAQ: Common questions about IP reputation attacks
How can I check my IP reputation?
You can check your IP reputation by looking up your address on public blocklists and watching for failed connections, throttling, or rejections from external services.
What causes IPs to get blacklisted?
IPs are blacklisted when they generate traffic associated with abuse, such as spam, automated scanning, or repeated failed connection attempts. This behavior can be caused by misconfigured services, compromised systems, or deliberate attacker activity.
What’s the difference between IP reputation and domain reputation?
IP reputation evaluates the behavior associated with a specific IP address, while domain reputation focuses on the sending domain itself. Both are often assessed together, but they rely on different signals and can be affected independently.
Can a shared IP affect my email deliverability?
Yes. When multiple users share the same IP, reputation is influenced by the combined behavior of everyone using it. If one sender generates spam or abusive traffic, it can negatively affect deliverability for everyone sharing that IP.
What does “warming up” an IP mean?
IP warm-up is the process of gradually increasing traffic from a new or previously flagged IP to rebuild trust with reputation systems.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN