How just-in-time access enhances cybersecurity

Over-privileged accounts are a valuable target for cybercriminals because standing permissions give attackers more time and opportunity to move laterally through a network without detection. A highly effective way to reduce the attack surface is to remove unnecessary privileges and avoid permanent access where it isn't required.
This article explains how just-in-time (JIT) access works and why it is an important component of modern security strategies. It covers key benefits, common risks, and practical implementation steps to help organizations adopt JIT access effectively.
What is just-in-time (JIT) access?
JIT access is the practice of granting privileged permissions only when a user needs them and automatically revoking those privileges once the task is complete. Unlike traditional role‑based models that assign permanent roles or always‑on privileges, JIT access keeps accounts in a default low‑privilege state and elevates them temporarily after verification.
JIT access is not the same as JIT provisioning. JIT provisioning typically focuses on creating or assigning accounts and entitlements on demand, which may persist for a defined period depending on implementation. By contrast, JIT access is session-based, granting temporary elevated permissions that expire when the session ends, reducing reliance on standing privileges.
JIT access is also sometimes confused with JIT compilation, a technique used by software runtimes to compile code at runtime. It’s unrelated to access control or privileged permission management.
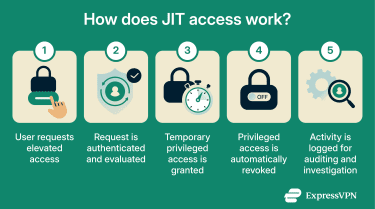
How just-in-time access works in practice
In practice, JIT access relies on a controlled elevation process. While implementations vary by platform and environment, a typical workflow includes the following steps:
- Baseline access: Users operate with standard permissions until privileged access is required.
- Access request: A request is submitted with details such as scope, duration, and business justification. The request is evaluated against a predefined policy.
- Controlled elevation: A privileged access management (PAM) platform or identity provider authorizes the request and provides time-limited access. Implementation commonly takes one of two forms: issuing temporary session credentials or adding the user to a privileged role/group for a fixed period.
- Automatic revocation: When the approved time window ends, or the session is closed, privileged access is automatically revoked. Any temporary accounts or entitlements created for the session (where applicable) are disabled or deleted in accordance with the system design.
- Monitoring and auditability: Session activity is captured through logs (and, where available, session recording) to support compliance requirements and incident investigations.
- Context-aware enforcement (optional): Some implementations evaluate conditions in real time (such as device posture, network location, risk signals, and role attributes) before approving access and, in more advanced implementations, throughout the session.
Types of just-in-time access
JIT access can usually be delivered in a few common ways. Each model provides temporary privileged capability, but they differ in how access is requested, granted, and scoped.
Justification-based access requests
In this model, users submit an access request that includes a business justification, the target system or resource, and the intended duration. Requests can be approved by a designated reviewer or evaluated automatically against policy, such as role, time constraints, or the sensitivity of the resource.
This approach is useful when privileged actions are infrequent or high-impact and require an explicit decision. It also produces a record of why access was granted, who approved it, and what scope was authorized, which supports audit and post-incident review.
Ephemeral and time-bound accounts
This approach may provide a privileged account, credential, or entitlement that exists only for the access period, depending on the system design. PAM tools can issue short-lived credentials on demand and disable or remove them automatically when the task concludes.
Some implementations use automatic rotation or one-time credentials to prevent reused secrets from being introduced into the environment. This model is often used for contractors and third-party vendors, where access should be isolated, time-limited, and easy to terminate without relying on manual cleanup.
Temporary privilege elevation in zero-trust environments
In a zero‑trust architecture, elevated roles are activated only when required conditions are met and remain constrained by policy while active. Requests are evaluated using contextual signals such as identity assurance, device health, network location, and risk indicators, and may require step-up authentication.
Because conditions can change during a session, some implementations re-check signals and revoke privileges if risk increases or the session context no longer matches policy. This model is well-suited to environments that already enforce conditional access and want privilege elevation to follow the same controls.
Benefits of just-in-time access
JIT access offers tangible security and operational benefits, which can translate into financial benefits. Essentially, reducing the duration and scope of privileged access limits the attack surface and helps prevent credential misuse.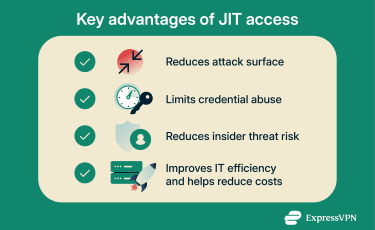
Reducing the attack surface with temporary privileges
When elevated access is granted only for a defined duration and limited to specific systems, there is less opportunity for dormant or always-on credentials to be abused. Time- and scope-bounded elevation also limits what a compromised credential can access, helping constrain lateral movement and reducing the risk of persistence beyond the approved window.
Preventing credential abuse and insider threats
Standing privileges not only increase exposure to external compromise but also make it easier for insiders to misuse access. Privilege creep (the gradual accumulation of permissions beyond what is necessary) often occurs when organizations don’t consistently remove access that is no longer required.
JIT access helps address this by requiring users to request elevation with a defined scope and justification, and by recording both the decision and the resulting activity for later review.
Short-lived elevation also reduces credential abuse by limiting when captured privileged credentials can be used.
Cost and operational efficiency of JIT models
JIT access can help streamline IT operations and reduce operational costs over time. By automating access requests and revocation, organizations can reduce the effort required to manually manage user roles and privileged permissions, easing administrative overhead for IT teams.
In environments with mature policies, routine elevation requests may be automatically approved based on predefined criteria, reducing delays in completing administrative tasks. JIT access can also help optimize license usage in systems where privileged tools or roles are licensed per user, by granting temporary access to occasional users rather than assigning permanent entitlements.
Security risks without JIT access
Without JIT controls, privileged access is often delivered through standing roles, long-lived credentials, or permanently elevated accounts. These patterns increase the likelihood that compromised or misused access will become high-impact.
Standing privileges and over-permissioned accounts
Standing privileges keep high-level access available at all times, including outside planned work windows. That constant availability increases the risk of “quiet” misuse: a compromised admin identity (including service accounts) can be exercised repeatedly without a fresh request or approval event that would normally trigger scrutiny.
Long-lived credentials tied to privileged identities (such as passwords, API keys, or durable tokens) also tend to spread through scripts, tooling, and shared workflows, which makes them harder to track and rotate. The result is a larger blast radius and more time for an attacker to operate before access is noticed or removed.
Increased exposure to phishing and malware
Phishing and social engineering often target standard user accounts to gain an initial foothold. If those accounts can be escalated easily, or already have elevated rights, attackers can move more quickly to actions such as installing malware, disabling defenses, and altering or deleting logs.
Environments built around long-lived privileged access make it easier for attackers to retain control and establish persistence after the initial compromise. JIT does not prevent phishing or malware, but it can reduce the damage those attacks can cause by limiting when and where privileged actions are possible.
How network security and VPNs strengthen JIT access
JIT access is most effective when paired with strong network security controls and encryption.
How encryption protects privileged sessions
Privileged sessions often carry high-value data such as credentials, commands, and configuration changes. Without transport encryption, this data can be exposed or altered in transit. A corporate VPN encrypts session traffic between the endpoint and an enterprise-managed gateway, protecting the confidentiality and integrity of privileged activity across untrusted networks.
PAM tools can also broker privileged connections through encrypted tunnels or session proxies without revealing passwords to the user. In both cases, encryption helps protect intercepted traffic by making it unreadable and more resistant to tampering.
Preventing MITM attacks on temporary admin access
Man-in-the-middle (MITM) attacks rely on tricking a client into trusting an attacker-controlled intermediary. A corporate VPN helps reduce this risk by enforcing gateway identity verification (for example, certificate-based authentication) and requiring approved cryptographic handshakes before a session is established.
Zero-trust network access (ZTNA) complements this by continuously validating the requesting user, device posture, and target resource, limiting opportunities for an attacker to insert themselves between endpoints during a temporary admin session.
Centralizing egress during high-risk access windows
Temporary elevated access can draw attention to exposed management endpoints. A corporate VPN allows remote administrative traffic to originate from controlled enterprise egress points rather than directly from a user’s public network location. This reduces direct exposure of endpoint network details and can minimize externally visible routing signals, such as exposed source IPs tied to individual endpoints.
It also makes it easier to apply consistent network controls (such as allowlists and geo-restrictions) at the gateway rather than across many individual endpoints.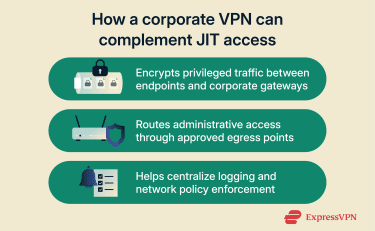
JIT access within a zero-trust and VPN security framework
Integrating JIT access with zero trust and a corporate VPN architecture strengthens policy enforcement and operational control. In this model, roles are activated only when needed, and access is conditioned on identity assurance, device compliance, and resource-level authorization.
A corporate VPN can serve as a controlled access path for remote connectivity, while JIT governs when and for how long privileges are active. Together, they support clearer enforcement boundaries: the network path is constrained to enterprise-managed gateways, and administrative entitlements are time-limited, auditable, and scoped to specific tasks.
How to implement JIT access in your organization
Implementing JIT access can be complex, especially when integrating with legacy systems and existing operational processes. A structured rollout helps reduce misconfigurations and makes it easier to expand coverage over time.
Steps for enabling just-in-time access
Adopting JIT access is typically an incremental change rather than a single cutover. Many providers recommend leveraging existing identity and/or PAM platforms to phase in JIT workflows, starting with the highest-risk roles and systems.
1. Privilege review and baseline mapping
Begin by identifying privileged identities and pathways, including user admins, service accounts, and built-in administrator roles. Discovery and inventory work should document where privileges exist, classify entitlements by function, and compare them against a defined baseline. This process helps surface orphaned accounts, unused access, and roles that have expanded beyond current needs.
2. Automation and access workflows
Define how elevation requests are initiated, approved, and fulfilled. JIT workflows commonly integrate with identity providers and ticketing systems to route requests to the correct approvers and enforce consistent policy. In mature implementations, low-risk, well-defined tasks may be eligible for policy-based automatic elevation, while higher-risk requests can be routed for manual review based on triggers such as role sensitivity, target system, or unusual access patterns.
3. Monitoring and logging privileged sessions
Centralize logging for elevation events and privileged activity so reviews do not depend on individual systems. Logs should capture who requested access, what was granted, the duration, and which resources were accessed.
Where supported, session recording and alerting for anomalous behavior help identify policy gaps and refine rules. Periodic access reviews remain important to confirm coverage, validate role definitions, and ensure controls operate as intended.
Common challenges and how to overcome them
Moving to JIT access can introduce practical obstacles, but each can be addressed with a defined rollout plan and consistent governance.
- Integration: Legacy applications and custom systems may not support modern identity controls or automated elevation. A PAM solution typically integrates with existing identity providers and ticketing systems where possible, with phased implementation to prioritize high-impact systems first.
- Complexity: Policy design can become difficult when different teams, roles, and resources require different rules. A common approach is to start with a small set of policies for the highest-risk roles, validate outcomes, and expand coverage iteratively.
- Monitoring and reporting: Privileged sessions can be hard to track when activity spans multiple platforms. Centralized logging and analytics help consolidate elevation events and session activity into a single view for investigation and compliance reporting.
- Inconsistent policies: If teams apply different request, approval, or time-limit practices, controls become uneven and less effective. Organization-wide standards for justification, approval, and maximum duration (enforced through automated workflows) help maintain consistency across environments.
Best practices for secure just-in-time access
JIT access works best when paired with controls that verify identity at elevation time, keep permissions tightly scoped, and provide reliable visibility into privileged activity.
Enforcing MFA for elevated sessions
Multi‑factor authentication (MFA) adds a second verification step beyond passwords. For privileged workflows, phishing-resistant factors such as hardware security keys or smart cards are commonly used.
Applying MFA at the moment of elevation (and, where appropriate, re-authenticating for especially sensitive actions) helps ensure that temporary privileges are issued only after strong identity verification.
Applying the principle of least privilege
Least privilege is achieved by limiting elevation to the minimum permissions required for a specific task, on the smallest practical set of resources, for the shortest workable time window. Clear role definitions, standardized request scopes, and predefined “task-based” privilege bundles help avoid broad or ambiguous elevation. Regular entitlement reviews help keep role templates aligned with current operational needs.
Using audit trails and continuous monitoring
JIT programs depend on reliable audit data for investigations, compliance, and control validation. Centralized logging should aim to capture elevation requests and approvals, what access was granted, session duration, and key actions taken.
Monitoring and alerting for unusual behavior (for example, unexpected targets, atypical timing, or high-risk commands) enable faster responses and help refine policies over time through periodic reviews.
FAQ: Common questions about just-in-time access
How does JIT access improve cybersecurity?
Just‑in‑time (JIT) access reduces reliance on standing privileges, making it harder for attackers to exploit dormant credentials. It also adds network accountability because each elevation request is logged and tied to a specific user and task.
What is just-in-time (JIT) authentication?
JIT authentication is a term sometimes used to describe a user’s identity at the moment they request elevated access, rather than relying solely on initial login authentication. It often involves multi‑factor authentication (MFA) and contextual policy checks before granting the session.
How is JIT access different from traditional access control?
Traditional access control policies assign static roles and privileges that remain active regardless of immediate need. Just-in-time (JIT) access evaluates access requests at the time of elevation and grants only the minimum privileges required for a specific session or task. Privileged access is then revoked automatically when the session or approved time window ends, reducing reliance on standing entitlements.
Can JIT access reduce third-party and vendor risks?
Yes. Just‑in‑time (JIT) access is particularly useful for managing third‑party contractors and vendors who require temporary privileged access. By granting elevation only for a defined scope and duration, JIT helps reduce the risk that external users retain access beyond an approved task.
How do I implement JIT access securely?
To implement just-in-time (JIT) access securely, require multi-factor authentication (MFA) or step-up authentication at privilege elevation, apply the principle of least privilege, and regularly audit data logs for elevation events and privileged activity.
Do VPNs help protect privileged access sessions?
Yes. A corporate VPN can help protect privileged access sessions by encrypting traffic in transit between the user and enterprise-managed gateways, reducing exposure to interception on untrusted networks.
It can also enforce connections to authenticated gateways (for example, using certificates), which helps reduce man-in-the-middle (MITM) risk, and it centralizes remote administrative traffic through controlled egress points where organizations can apply consistent access policies, logging, and monitoring.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN