What is sextortion, and how do you recognize, avoid, and respond to it?
Sextortion is a form of blackmail in which someone threatens to share real or fabricated intimate images, videos, or messages unless their demands are met. These threats are often delivered through direct messages and are designed to create urgency by triggering fear, embarrassment, or panic.
The extortionist may pressure the target to send additional content, perform sexual acts in person or on camera, or send money. The threat typically involves exposing images or videos to friends, family members, employers, or the public if the victim doesn’t comply.
How do sextortion attacks work?
Sextortion attacks can originate from a stranger or someone the victim knows personally, such as a former partner. In many cases, the extorter makes contact with the target, stating they’ve obtained explicit content through one of the following sources:
- Access to a device or account.
- Communication on social media, gaming platforms, messaging apps, or dating services.
- Previous relationships where images or videos were shared consensually.
- Nonconsensual images or videos captured without the person’s knowledge.
- Recordings of live video interactions, such as video calls.
Once contact is established, the perpetrator threatens to distribute the material unless the victim complies with specific demands. These demands may involve financial gain, but they can also include control, revenge, humiliation, or ongoing exploitation.
Common sextortion tactics
A range of methods are used to obtain compromising material or to create the impression that such material exists. Tactics can vary based on how contact is initiated, which channels are used, and what is demanded in return.
Fake threats
Some sextortion campaigns rely on deceptive messages and fake threats to pressure recipients into complying with extortion demands. To make the threat appear credible, the messages often include personal details such as a name, email address, or home address. In some cases, the sender claims that malware was used to capture webcam footage of the recipient engaging in sensitive activities, such as viewing adult content.
In reality, extortionists may not have any evidence to support these claims. Instead, they rely on fear and embarrassment to provoke a reaction, using publicly available information or data from past breaches to personalize the messages.
Malware and spyware infiltration
Some sextortion campaigns start with installing malware or spyware onto a target’s device. This can happen through deceptive downloads, malicious attachments, or links that appear legitimate. Once installed, the malware may access files, capture screenshots, or activate the device’s camera without the user’s knowledge. (Note, however, that many sextortion claims about webcam hacking are bluffs.)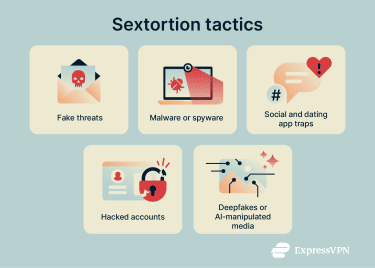
Attacks via social media and dating apps
Many sextortion schemes begin on social platforms, gaming chats, dating apps, or messaging apps such as Snapchat, sometimes as part of a broader online dating scam. The perpetrator typically creates a fake profile and presents themselves as friendly or attractive to establish trust. Over time, they encourage private conversations and may request intimate photos or suggest moving to video chats.
If the target shares compromising material or participates in a video interaction, the content may be saved or recorded. The threat of releasing these images or videos is then used to exert pressure.
Hacked accounts
Some sextortion schemes involve unauthorized access to online accounts or false claims that such access has occurred. In these cases, perpetrators may assert that they have compromised a victim’s email, social media, cloud storage, or other accounts to obtain private images.
AI and deepfakes
Deepfake technology may be used by perpetrators to generate realistic-looking explicit images or videos, even when the victim never created or shared such content. In these cases, publicly available photos or videos from social media profiles, material shared during online interactions, or footage captured during video calls are used with AI tools to fabricate explicit content, which is then leveraged in threats demanding payment or compliance.
Many AI platforms and image-generation services have safeguards designed to prevent the creation of non-consensual sexual content. However, in early 2026, investigations into widely used AI chatbots revealed gaps in moderation that allowed for the generation of non-consensual sexual content. As AI technology evolves, protection measures are constantly being updated to meet new challenges.
Large-scale data leaks from AI image-generation services have also exposed how easily intimate and manipulated images can be created, stored, and misused. In late 2025, cybersecurity researcher Jeremiah Fowler found an unsecured database linked to an AI image generator that publicly exposed over one million user-generated images, many of them explicit and AI-manipulated.
How to protect yourself from sextortion
Staying safe from sextortion requires awareness, careful sharing, and knowing when to ask for help. Here are practical steps you can take:
- Think before you share: Even when content is shared consensually and in good faith, circumstances can change. Images or videos shared privately may later be saved, redistributed, or misused without consent.
- Be careful with strangers: Block or ignore unexpected messages from people you don’t know, and be cautious if someone tries to move the conversation to a different platform.
- Verify identities: People can pretend to be anyone online. Photos, videos, or profiles aren’t proof of identity. Scammers may steal images or even take over accounts to trick victims. Use a separate channel, like calling a known phone number, to verify identities.
- Use strong passwords: Strong passwords make it much harder for extortionists to access accounts and steal explicit content. Consider using a password manager to safely store and generate complex passwords for all your accounts.
- Use antivirus software: An effective antivirus tool can detect spyware and other malware, preventing perpetrators from capturing explicit content with your camera or stealing sensitive data from your device.
- Secure your devices: Keep your devices and webcams turned off when not in use. Be cautious with emails, messages, or links from unknown senders, as they can contain malware or spyware. Avoid storing not-safe-for-work (NSFW) content on your devices to reduce the risk of it being accessed or leaked.
- Use privacy settings: Limit who can see your social media accounts and posts. The less public information extortionists can access, the harder it is for them to target you.
Note: While a virtual private network (VPN) encrypts your connection and hides your IP, it can’t prevent extortion if you voluntarily share content or if an account is compromised via social engineering.
Educating teens about sextortion
When young people are aware of online risks, they’re more likely to speak up if something feels off. Encouraging open conversations about internet use helps them identify potentially dangerous situations online before they escalate.
How to talk openly about online safety with your children
Here are simple ways you can start open, supportive conversations about sextortion and online safety:
- Explain how sextortion starts: Talk about how predators often contact young people through social media, gaming platforms, or messaging apps. Explain that extortionists may act friendly or supportive at first and then pressure them to share private images or information.
- Set clear rules about sharing: Tell them never to share intimate photos, videos, or personal details online or over text. Make it clear that even people they trust can misuse shared content.
- Normalize asking for help: Encourage them to speak up if a message, request, or conversation makes them uncomfortable. Reassure them that they won’t get into trouble for asking questions or reporting a problem.
- Reinforce that online identities can be fake: Remind them that people can pretend to be anyone online. Explain that photos, videos, and profiles don’t prove someone’s identity and that scammers often lie to gain trust.
- Keep the conversation ongoing: Check in regularly about online activity and digital interactions instead of having one serious talk.

Warning signs parents should know
The warning signs below can help you spot possible sextortion early and take action quickly:
- Sudden secrecy around devices or online activity: Your child may hide their screen, close apps, or turn off their computer when you walk into the room. They may delete messages, images, or browsing history, or refuse to talk about what they do online.
- Sudden increase in online activity: Your child may stay online for long periods, especially late at night. They may seem tense or distracted while using their phone or computer.
- Online contacts who avoid being seen: Your child may talk frequently about an online friend or relationship, but when you ask about meeting them, video chatting, or confirming who they are, they always have excuses. Ongoing reluctance to show their face or identity can be a red flag for grooming that may escalate into sextortion.
- Strong emotional or behavioral changes: Your child may become withdrawn, anxious, fearful, angry, or unusually irritable. They may show mood swings, sadness, or signs of depression.
- Declining school performance or daily functioning: You may see a drop in grades, loss of interest in hobbies, or trouble sleeping. These shifts often signal ongoing stress.
- Money concerns or urgent requests: Your child may ask for money urgently or without a clear reason.
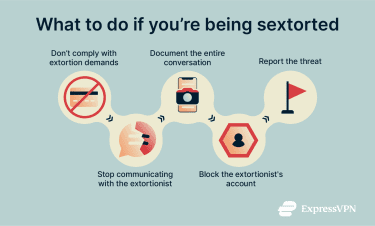
What to do if you are targeted by sextortion
Follow these steps to protect yourself, get help, and stop the extortion from getting worse:
- Don’t pay or send gift cards: If the sextortionist asks you to send them money, don’t. Paying can encourage them to make more demands and doesn’t guarantee they’ll stop threatening you.
- Document the threats and gather evidence: Take screenshots of all messages, profiles, and details about the threats you receive. Save the dates, times, usernames, and any links involved. This information can help law enforcement when you report the incident.
- Report the threat to the platform: Report the extortion attempt to the platform where you were contacted. Many social networks and apps have built-in reporting tools.
- End the chat: After documenting evidence and reporting the threat, stop all contact with the person trying to extort you. There’s no guarantee that material won’t be shared at this stage, but continued engagement often leads to repeated or escalating demands.
- Block the account: Use the platform’s settings to block the extortionist’s account. Blocking prevents them from contacting you again and limits their access to your profile or content.
Where to report sextortion
In addition to reporting the incident to the platform where it occurred, you should also report it to the appropriate authorities as soon as possible. Remember, you’re not the one at fault, even if you willingly shared sensitive material with the extortionist: the wrongdoing lies with the person trying to exploit or threaten you. Law enforcement and support services handle cases like this regularly and can help you.
In the U.S., victims of any age can report digital extortion cases to the Internet Crime Complaint Center (IC3). For both online and in-person sextortion, you can call your local FBI office or toll-free at 1-800-CALL-FBI.
Cases involving minors should be reported to the nonprofit National Center for Missing & Exploited Children (NCMEC) through its CyberTipline. It operates 24 hours a day, 7 days a week. The Internet Crimes Against Children (ICAC) task force also provides jurisdiction-specific hotlines and downloadable PDF resources.
How to remove explicit online images
For adults targeted with non-consensual intimate images online, StopNCII.org offers a free, privacy-focused tool designed to help prevent and reduce the spread of those images. Operated by the U.K.-based Revenge Porn Helpline and its parent charity South West Grid for Learning (SWGfL), the platform lets users create a unique digital “hash” (a kind of fingerprint) of their private image or video directly on their device, without uploading the actual content. That hash is then shared with participating tech companies, which can use it to detect, block, or remove matching images if they are uploaded or redistributed across platforms. Although StopNCII.org is rooted in the U.K., any adult anywhere in the world who meets the criteria (the image is of them, was taken when they were 18 or older, and they have access to it) can use the service to help protect their content online.
For underage victims, Take It Down is a free service operated by NCMEC that helps people remove or limit the spread of intimate images shared without their consent. The tool works in a way similar to StopNCII.org, by creating digital hashes of the images or videos on the user’s own device, allowing participating platforms to detect and block those files.
Seek legal support
Getting legal advice helps you understand your rights and options after a sextortion attempt. A lawyer or legal advocate can guide you through reporting processes, privacy protections, and steps to protect your digital reputation. Law enforcement may also connect you with victim support services such as the Cyber Civil Rights (CCR) (for U.S. residents) that can help you navigate the aftermath of the incident.
FAQ: Common questions about sextortion
What legal actions can you take against sextortion?
You can report sextortion as a crime to law enforcement so they can investigate and charge the offender under applicable laws. In the U.S., federal authorities like the FBI and Homeland Security Investigations (HSI) pursue cases of online sexual exploitation and coercion and may prosecute criminals who coerce victims or blackmail them for money or images.
How can parents protect their children from online sextortion?
Parents can protect their children by educating them about safe online behavior, monitoring their online activity, and encouraging open communication about uncomfortable interactions.
Are sextortion cases increasing?
Yes, many authorities report a clear increase in sextortion and related extortion crimes. In 2024, the FBI received nearly 55,000 reports tied to sextortion and extortion, with reported financial losses of about $33.5 million. This marked a 59% increase in reports compared to 2023.
How is sextortion different from other cybercrimes?
Sextortion differs from other cybercrimes because it combines online interaction with threats to expose intimate material to coerce victims into sending more content or paying money. While other cybercrimes may focus on financial theft or hacking, sextortion uses personal material as leverage to manipulate victims.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN