What is a cross connect in a data center?
Data centers are built to handle massive volumes of information moving between companies, cloud services, and networks. Inside data centers, this exchange happens through carefully managed infrastructure designed for performance and security.
One key component of that setup is the cross connect: a dedicated, private link between two entities colocated in the same facility, such as a business and a cloud provider. It enables fast, reliable, and secure data transfer without using the public internet.
In this guide, we’ll look at how cross connects work, what benefits they offer, and how they compare to other connectivity options used in data centers today.
Understanding cross connects
A cross connect is a physical, point-to-point cable link between two hardware endpoints inside a data center. These endpoints are usually housed in racks: standardized metal cabinets that hold servers, switches, and other equipment.
Cross connects are common in colocation environments, where multiple organizations rent rack space in the same facility to host their infrastructure. Because both parties are physically present under one roof, technicians can run a dedicated cable between their racks through patch panels and structured cabling systems.
Some cross connects link a company’s equipment to a cloud on-ramp: a physical access point to a cloud provider’s private network, such as AWS Direct Connect or Azure ExpressRoute.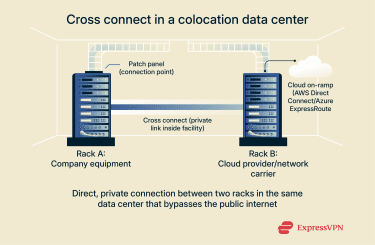
Unlike internet-based connections that route traffic through external networks, a cross connect keeps data on a private, predictable path inside the data center, reducing latency and improving security. Depending on bandwidth and distance requirements, the link typically uses fiber-optic or copper cabling.
Cross connects are what make colocation environments so powerful. They let businesses link their infrastructure directly to cloud providers, internet service providers (ISPs), or partners housed in the same facility, without relying on external routing. This setup helps minimize costs while improving both speed and reliability for data exchange between colocated systems.
Benefits of cross connects in data centers
Cross connects come with multiple advantages that make them essential to modern data centers. Here are some of the most significant ones.
Enhanced security and privacy
Because cross connects keep data on a private, point-to-point path within the facility, sensitive traffic never passes through public networks. This isolation reduces interception risk and strengthens confidentiality. It’s especially valuable when connecting to partners, carriers, or cloud on-ramps that handle critical workloads.
Faster and more reliable data transfers
Cross connects eliminate unnecessary network hops, allowing traffic to move quickly and predictably between endpoints. With fewer intermediaries, latency drops and congestion becomes less likely.
Since the connection stays inside the data center’s infrastructure, it remains stable, which is ideal for real-time applications and high-volume workloads that demand consistent performance.
Improved network management and stability
Cross connects give IT teams direct control over how data moves inside a data center. Clear, physical links between systems make it easier to monitor traffic, adjust routes, and prevent unnecessary external transfers. With an organized layout, teams can spot issues faster and resolve them before they affect operations.
Because these connections are dedicated and predictable, performance remains steady even during peak activity. Cross connects support consistent communication between servers, providers, and storage systems, reducing potential failure points and helping maintain high uptime and stable performance.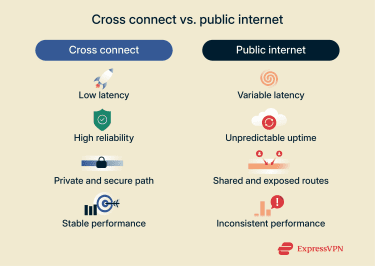
Business advantages of cross connects
Beyond the technical benefits, cross connects also deliver measurable business value by improving performance efficiency, flexibility, and cost control:
- Lower latency for smoother operations: A private connection keeps data away from congested public networks. Traffic moves faster between partners and systems, improving real-time workloads and overall responsiveness.
- Reliable uptime with guaranteed service levels: Dedicated connections inside the data center deliver predictable performance. Many providers include uptime guarantees through service level agreements, giving businesses confidence that services stay available when needed most.
- Higher security and stronger compliance: A closed, physical path protects sensitive data from public exposure. Access controls and authorization layers create a secure channel that aligns with strict privacy and compliance standards.
- Operational efficiency and cost savings: Stable, direct connections reduce bandwidth costs and minimize downtime, helping teams maintain consistent workflows without relying on expensive external routing.
Types of data center cross connects
Every data center has its own way of keeping systems connected. Cross connects can use different kinds of cables and setups depending on what the network needs: speed, distance, or capacity.
Fiber cross connects
Fiber cross connects transmit data using light rather than electrical signals, which allows them to support very high speeds over longer distances. This makes them well suited for moving large volumes of data reliably within modern data centers, even as network demands scale.
Because fiber can carry high-bandwidth traffic with minimal signal loss, it reduces the need for repeaters or signal-boosting equipment. That consistency is especially important for performance-sensitive workloads such as analytics platforms, financial systems, and cloud services.
Fiber connections also remain stable in dense, cable-heavy environments common in data centers. Thanks to their speed, range, and reliability, fiber cross connects are the standard choice for high-performance and scalable network infrastructure in most modern facilities.
Copper cross connects
Copper cross connects remain widely used because they combine simplicity, durability, and cost-effectiveness. They link network components, such as switches and servers, through conductive copper cables that perform well over short distances. This cabling supports stable data transmission and integrates easily into existing setups without complex installation or high expense.
However, copper has practical limitations compared to fiber. As bandwidth demands increase, copper connections are more constrained in both speed and distance, which can make them less suitable for large-scale or high-performance deployments. Signal quality also degrades more quickly over longer runs, limiting how far copper cross connects can reliably extend within a facility.
For these reasons, copper cross connects are typically used for shorter, lower-bandwidth connections where cost and simplicity matter most, while fiber is favored for high-capacity links, longer distances, and environments that need to scale over time.
Wireless cross connects
Wireless cross connects are a theoretical concept that aims to replace physical cabling with light- or radio-based communication inside data centers. In principle, any system that works over wired links can transmit wirelessly, but real-world cross connections demand extremely low latency and high bandwidth, levels that current wireless technologies can’t reliably deliver.
Most research in this area focuses on free-space optical (FSO) systems, such as LiFi or laser-based optical links, where transceivers use beams of light to transfer data through open air between racks.
However, these systems face practical challenges: clear line-of-sight requirements, complex alignment, power demands, and sensitivity to obstructions. As a result, wireless cross connects remain largely experimental, appearing only in laboratory environments and research prototypes rather than commercial data centers.
Comparison of data center cross connect types
Here’s a quick comparison of the main types of data center cross connects, including their medium, speed, range, and best use cases.
| Description | Speed capacity | Typical distance | Cost level | Best use/application | |
| Fiber cross connect | Glass or plastic strands transmitting light | Up to 400Gbps and beyond | Up to 985 feet / 300 meters (can support much longer distances) | Higher upfront, low maintenance | High-performance workloads, cloud peering, data replication |
| Copper cross connect | Electrical signals over twisted copper pairs | Up to 10Gbps (short range) | Up to 330 feet / 100 meters | Affordable and easy to install | Short-distance server links, rack clusters |
| Wireless cross connect | FSO or radio-frequency signal | Variable (typically up to 10Gbps) | Line-of-sight, limited range | Experimental | Research or temporary setups where cabling isn’t possible |
Deployment of cross connects
Deployment depends on where the link needs to land. Within a data center, cross connects can link equipment racks, connect to carrier panels in shared interconnection spaces, or extend to enterprise networks across multiple sites.
Within data centers
Inside a facility, a cross connect is the physical cable that links your equipment rack directly to another party’s rack. This private connection creates a dedicated data path between two endpoints, often bypassing shared meet-me areas for faster and more secure traffic flow.
Setting up such a link is a precise, operator-managed process. The requesting customer (the A-side) submits detailed location information (cage, cabinet, patch panels, and port numbers) for both their own and their partner’s (Z-side) equipment. Technicians then use these details to terminate the cable accurately and safely.
A valid letter of authorization (LOA) from the Z-side is always required. This document grants permission to access the partner’s ports and authorizes the operator to complete the installation on their behalf.
In telecommunication rooms
Beyond direct rack links, the telecommunication room, known as the meet-me room (MMR), acts as the neutral hub where networks interconnect. It’s essentially the trading floor of connectivity, where carriers, cloud on-ramps, and service providers terminate their physical infrastructure.
When you connect to one of these providers, your cable path routes through the MMR. Instead of each provider running cables to every customer cage, the facility operator installs cross connects between your rack and the provider’s panel within this secure, shared room.
This approach offers maximum flexibility. It simplifies management, shortens provisioning times, and allows businesses to access a wide ecosystem of providers (from Tier 1 carriers to specialized networks) without changing their internal layout. It also makes switching or upgrading services straightforward while keeping existing infrastructure intact.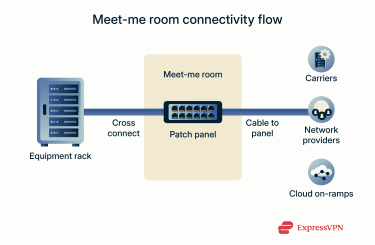
Enterprise network environments
A cross connect doesn’t only serve systems within the same facility; it can also extend the data center’s private environment into an enterprise network. This approach bridges the gap between colocation infrastructure and a company’s offices, campuses, or production sites.
To achieve this, enterprises typically use dedicated carrier circuits that link their on-premises routers to a designated patch panel in the data center’s MMR. The operator then installs the final cross connect, completing the private route between the carrier’s circuit and the customer’s equipment.
This setup forms a reliable wide area network (WAN) extension, giving employees fast and predictable access to hosted applications and data through the data center’s infrastructure instead of the public internet. Businesses rely on this method for data replication, disaster recovery, hybrid cloud integration, and other latency-sensitive operations.
Cross connect vs. other connectivity solutions
Cross connect is often mentioned alongside other networking terms that sound similar but refer to different concepts. Here’s how they differ:
Cross connect vs. direct connect
Despite their similar names, these two serve different purposes:
- Cross connect: It’s the physical cable inside a data center that links two parties, like your rack and a provider’s panel.
- Direct connect: It’s a cloud provider’s private connectivity service that uses that physical link to reach its private network.
In short: the cross connect is the hardware, and direct connect is the service delivered through it.
Cross connect vs. interconnect
At the cabling level, an interconnect is a direct wiring link that connects network equipment through a single patch panel, essentially a distribution point. A cross connect, on the other hand, adds an extra layer of patching through additional panels that mirror equipment ports. This design creates a dedicated patching area, allowing technicians to easily reconfigure connections without touching the active hardware.
At the network level, interconnection refers to the broader strategy of linking networks, carriers, and cloud providers within or between facilities. The cross connect is the specific physical cable that enables one of those connections inside the data center.
Cross connect vs. leased lines
Both options provide private connectivity, but their models and costs differ.
- Leased line: Also called a dedicated internet access (DIA) circuit, a leased line is a telecom-managed connection that spans geographic distances and includes the local loop: the carrier-owned segment between your premises and their network.
- Cross connect: This, by contrast, exists entirely within a data center. If your carrier is already present in the same facility, you avoid the expense of that local loop.
This makes cross connects the most cost-effective way to achieve high-bandwidth, low-latency communication with carriers, clouds, or partners already in the building.
Cross connects and VPN: How they work together
A cross connect and a corporate virtual private network (VPN) protect data in different but complementary ways. The cross connect secures the physical path your data travels on, while the VPN protects the information itself by encrypting it. Together, they form two layers of network security: one at the hardware level, the other at the software level.
Note: In this section, VPN refers to corporate VPNs, private networks used by organizations to connect offices, employees, and data centers securely. This is different from commercial VPNs like ExpressVPN, which are designed for individuals who want to protect personal data and browsing activity online.
Do cross connects replace VPNs?
The short answer is no, a cross connect doesn’t replace a VPN. They fulfill fundamentally different security needs within the network.
A cross connect guarantees that data travels over a private, dedicated cable path instead of the public internet. This ensures network isolation and predictable performance, but it doesn’t encrypt the data being transmitted.
A VPN adds that missing layer of protection by encrypting data before it leaves a secure environment. If information moves between data centers or to remote users, the VPN ensures that even if someone intercepts the traffic, they can’t read it.
In short, the cross connect keeps your data on a controlled route, and the VPN keeps it unreadable. Both are essential for a complete, multilayered security strategy.
Using cross connects to enhance VPN performance
Corporate VPNs often rely on the public internet, where congestion and variable routing can cause high latency and packet loss. When a VPN tunnel runs over a cross connect, the traffic stays within a private, low-latency fiber link instead.
This setup eliminates most internet-related delays, stabilizes performance, and maintains encryption security inside a controlled environment. The result is faster VPN throughput, reduced packet loss, and a consistent user experience, especially for critical workloads that require both speed and security.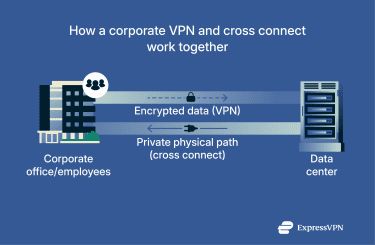
Security and compliance considerations
A cross connect offers Layer 1 (physical layer) security by enforcing physical isolation of the communication path. Because it uses a dedicated cable between two endpoints, traffic is removed from shared infrastructure where congestion or external threats are more likely. In effect, the path becomes auditable and less exposed to interception within the facility.
That said, physical security alone isn’t enough for compliance. Frameworks like the Health Insurance Portability and Accountability Act (HIPAA), Service Organization Control (SOC) 2, and Payment Card Industry Data Security Standards (PCI DSS) demand logical and administrative controls too, such as encryption, access management, logging, and monitoring. Even when using a cross connect, your organization must apply these controls on its systems and data.
It’s important to note that a cross connect doesn’t automatically grant compliance status. It supports compliance by giving you a verifiable, isolated path for sensitive traffic, but the rest of your stack (applications, encryption, identity, and policies) has to meet the standards as well.
Because the path is private and auditable, regulators often see it as a strong foundational control in sensitive environments. Combined with higher-layer protections, it helps reduce risk and streamline the audit process.
Challenges with cross connects
While a cross connect offers the gold standard in performance, setting one up can introduce certain challenges related to cost, latency, and operational management.
Common latency issues
Even with a dedicated, high-speed cross connect in place, latency issues can still occur when the physical infrastructure is faulty. A cross connect is a physical cable, and its performance relies heavily on proper installation and components:
- Wrong cable type: Using the incorrect media, such as multi-mode fiber for a long run that specifically requires single-mode fiber, causes rapid signal loss and jitter, defeating the entire low-latency purpose.
- Poor termination: Technicians must splice and terminate fiber connectors precisely. Incorrect or poor terminations introduce signal loss and measurable latency, undermining your performance gains.
- Contamination: Any contamination, such as dust or oils on the fiber end-faces, degrades signal integrity and increases bit error rates, forcing the system to retransmit data and spiking latency.
Cost considerations and limitations
A cross connect in a data center offers clear value, but the financial structure requires careful upfront planning. You need to look beyond the initial price and consider the full impact on your data center connectivity:
- Initial setup fees: A fiber cross connect requires an installation fee (non-recurring charge, or NRC), which can be substantial upfront. This fee ties your data center cabling to a physical location, giving you less immediate liquidity than purely virtual solutions.
- Monthly fees and redundancy: You pay a low monthly recurring charge (MRC) for the private network connection itself. However, for high availability, you must budget for redundancy. This means you must buy two connections to get a fully diverse (redundant) path.
- The cost-benefit balance: The immediate NRC and MRC must be weighed against the significant long-term savings gained from bypassing high-cost local loops and expensive public cloud egress fees.
Best practices for implementing cross connects
Establishing a reliable cross connect requires both strategic foresight and disciplined execution. The following best practices cover planning, deployment, and long-term management steps to help ensure stable, high-performance connectivity.
Planning and capacity considerations
Most cross-connect issues can be avoided through strong planning and attention to detail.
1. Manage costs strategically
- Calculate the total cost of ownership (TCO) rather than focusing only on setup or monthly fees.
- Factor in the long-term savings from bypassing telecom loops and reducing cloud egress costs.
- Use automated LOA workflows and asset tracking systems to prevent provisioning delays.
2. Design for capacity and reliability
- Project your capacity needs two to three years ahead, not just for current workloads.
- Always build in redundancy by ordering two physically separated cross connects for failover protection.
- Define demarcation points (the exact A-side and Z-side patch panel ports) before ordering. Clear documentation prevents costly delays and misconfigurations.
3. Maintain quality assurance
- Enforce rigorous Layer 1 testing for continuity, power loss, and signal integrity.
- Follow data center cabling standards strictly to prevent contamination or poor terminations from impacting latency.
Step-by-step implementation guide
Successful implementation requires strict process adherence to preserve low latency.
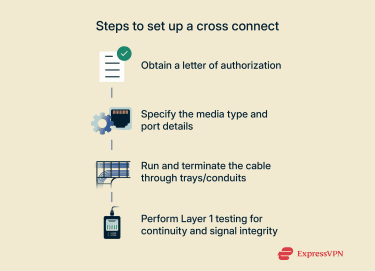
- Authorization: Obtain a formal LOA from the Z-side partner before submitting the order to the facility operator.
- Order and provisioning: Submit the order specifying the media type (usually fiber cross connect), connector type, and the precise A-side and Z-side ports. The operator uses this detail to provision the physical cable.
- Physical installation: The technician physically runs the data center cabling through protected pathways (trays or conduits) and terminates the link at the specified patch panel ports.
- Testing and verification: Teams perform rigorous Layer 1 testing (continuity, power loss, and signal integrity) to ensure the newly installed private network connection performs to specification before accepting the service.
Monitoring and managing cross connects effectively
Monitoring is essential because a cross connect is a passive, physical link that only functions if the cable remains intact and clean. Implement proactive monitoring of the active equipment on both ends to detect performance degradation immediately.
Log all changes: every time a technician touches the data center cabling or patches the link, log the activity against the colocation cross connect circuit ID. This due diligence ensures clear audit trails and simplifies troubleshooting when issues arise.
FAQ: Common questions about cross connects
What is an example of a cross connect in a data center?
A common example is a local cross connect linking your server rack directly to a cloud provider's router or a carrier's patch panel inside the same building. This dedicated physical link guarantees private communication, often bypassing shared meeting areas for ultra-low latency.
How do you implement a cross connect in a data center?
Implementation requires obtaining a letter of authorization (LOA) from the partner you're connecting to (Z-side) first. Then, you submit the order specifying the media type and precise patch panel ports. The facility operator runs the data center cabling, and finally, you enforce rigorous Layer 1 testing (like light link verification) before accepting the service.
What are the costs associated with cross connects?
Cross connects involve two primary charges: a non-recurring charge (NRC) and a low monthly recurring charge (MRC) for the physical link. To manage this, you must weigh these fees against the long-term cost savings gained by eliminating expensive local loop charges and high public cloud egress fees.
What are the challenges of using cross connects?
The main challenges are financial (the high initial setup fees) and operational. Operational challenges include securing the letter of authorization (LOA) in time and technical issues like latency caused by faulty data center cabling (e.g., poor terminations or contamination), which degrades signal integrity.
Do I still need a VPN if I use a cross connect?
Yes. A cross connect provides physical security by isolating the traffic from the public internet, but it does not provide data encryption. You need a VPN to layer encryption over the private link, ensuring data integrity and end-to-end protection, especially when connecting remote users or other off-site networks.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN