What is swatting and how can you prevent it?
Swatting is a dangerous form of harassment that exploits emergency services. It involves making false reports to trigger armed police responses at a specific address. These incidents often target streamers, journalists, or people involved in online disputes and can have severe consequences.
Beyond the immediate physical risks, swatting exposes critical vulnerabilities in digital privacy, demonstrating how personal data misuse can lead to dangerous real-world outcomes. This guide explains what swatting is and how it typically happens before outlining effective privacy practices to help reduce your exposure to these attacks.
What is swatting and why is it dangerous?
In the following sections, we'll break down the key terms and technical elements involved in swatting.
What does “swatting” mean?
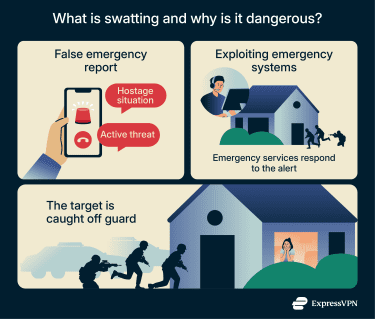 The term "swatting" derives from Special Weapons and Tactics (SWAT) teams, which are specialized U.S. police units trained for high-risk situations. Swatting means deliberately calling in a fake severe or ongoing emergency to send these units to someone’s location. The goal is usually to cause chaos or intimidate or scare the target.
The term "swatting" derives from Special Weapons and Tactics (SWAT) teams, which are specialized U.S. police units trained for high-risk situations. Swatting means deliberately calling in a fake severe or ongoing emergency to send these units to someone’s location. The goal is usually to cause chaos or intimidate or scare the target.
How swatting works
Swatting exploits trust in emergency systems. An attacker reports a serious threat at a specific address, prompting police to respond quickly. Even though the report is false, the real-world response catches the target off guard and poses a real danger.
Tools and information used in swatting attacks
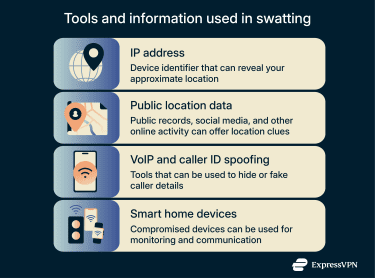 Swatting incidents typically leverage widely accessible tools and publicly available information rather than advanced technical skills. Some common elements include:
Swatting incidents typically leverage widely accessible tools and publicly available information rather than advanced technical skills. Some common elements include:
- IP address: An IP address is a label assigned to your device when you connect to the internet, mainly used to route traffic. It can reveal your general area (like a city or region) based on your internet service provider (ISP), but it doesn’t provide an exact physical location. IP-based location data is often imprecise and usually needs to be combined with other information to identify your specific whereabouts.
- Publicly available location data: Attackers may gather location clues from public social media posts, livestreams, geotagged photos or videos, app activity, online forums, public records, and any other online content that reveals your whereabouts or routines.
- Voice over Internet Protocol (VoIP) and caller ID spoofing: Attackers often use VoIP services (technology that allows calls over the internet) and caller ID spoofing techniques to disguise their real phone numbers. These methods help obscure their location and complicate efforts to trace the source of false emergency calls.
- Compromised smart home devices: In some cases, threat actors may exploit vulnerabilities in smart home devices such as security cameras, smart assistants, or doorbells to monitor occupants’ activities or communicate with emergency responders.
Learn more: What can someone do with your IP address?
How swatters can obtain your personal information
In addition to looking for public information online, swatters often rely on social engineering techniques to gather personal data needed for targeting. This includes methods such as:
- Phishing: Fraudulent attempts to trick individuals into revealing sensitive information through deceptive emails, messages, or websites. Learn more in our guide to preventing phishing attacks.
- Use of doxxed information: Swatters may exploit data that has been previously exposed or published through doxxing, which is the collection and sharing of private information without consent and can include someone’s location.
- Impersonation: Pretending to be a trusted individual or organization, typically online, to extract information from the target or their contacts.
They search for patterns, routines, and connections to identify the person and reveal their physical location. Even small details that seem harmless on their own can become dangerous when combined.
Is swatting illegal?
Yes, swatting is illegal in many countries and is recognized as a serious criminal offense. It typically violates laws related to making false reports, misuse of emergency services, and endangering public safety. Legal consequences can be severe, including criminal charges and penalties.
Legal frameworks vary by jurisdiction, and penalties depend on the specific circumstances of each case. Swatting prosecutions often emphasize the serious risks to public safety and the misuse of emergency resources.
How to recognize and respond to swatting threats
Swatting threats typically originate online, often as part of broader harassment campaigns before escalating to offline incidents.
Warning signs to watch for
Swatting is often linked to cyberstalking and targeted harassment. Common warning signs include:
- Repeated harassment or unwanted communications: Continuous messages, comments, or interactions intended to intimidate or provoke.
- References to the police or law enforcement: Threats or messages mentioning police intervention, SWAT teams, or emergency responses.
- Indications that someone knows your personal location or address: Explicit or implied references to your home, workplace, or routines that suggest your physical whereabouts have been identified.
- Unusual or intrusive interest in your daily life and activities: Attempts to track or monitor your schedules, travel plans, or habits through online or offline means.
- Attempts to provoke strong emotional reactions: Messages designed to elicit fear, anger, or distress, potentially to manipulate your response or prompt a public reaction.
Who does swatting target?
Swatting can target a wide range of individuals, including high-profile gamers, streamers, journalists, and public figures with a visible online presence. While incidents involving well-known individuals often receive media coverage, swatting also affects everyday people who may have less public visibility.
According to estimates cited by the Anti-Defamation League, there were about 1,000 swatting incidents in the U.S. in 2019, though exact tracking has been limited because no central database existed at the time.
How to prevent swatting
Preventing swatting focuses on limiting personal data and reducing how much information about you is publicly accessible. The steps below outline practical techniques and tools for minimizing data exposure.
Best practices for online privacy
Remove your personal data from the internet
Swatting often relies on personal information that is publicly available, leaked, or aggregated from multiple sources. Reducing your digital footprint makes it harder for malicious actors to identify your location or target you. Here are a few ways to do so:
- Use data removal services: Data removal services help identify and remove personal information from data broker sites and people-search databases that collect and resell personal data. ExpressVPN’s Identity Defender includes a data removal service that automates opt-out requests and provides ongoing monitoring, reducing the effort required to manage your exposure.
- Review your social media accounts: Check your profiles for personal information, old posts, or outdated content that could reveal sensitive details.
- Close unused accounts: Review old accounts on platforms, services, or forums you no longer use and close them to prevent potential data exposure.
- Check other personal data sources: Look for personal information in public records, professional listings, or old resumes that could be contributing to your digital footprint.
Monitor the dark web
Dark web monitoring services can help identify whether your personal information has been exposed through data breaches or illicit data markets. These services typically monitor for items such as email addresses, usernames, and financial details associated with known breach sources.
Alerts can help you respond quickly, such as updating compromised passwords, securing affected accounts, or contacting relevant service providers. While dark web monitoring doesn’t prevent breaches, it can support faster response and help limit the downstream risks associated with leaked personal information.
Be cautious with third-party apps and services
Many apps and websites request more personal data than they actually need. Limiting the information you share helps reduce the risk of exposure or misuse.
Only grant permissions that are essential for the site or app’s function; for example, avoid giving location access unless it’s truly necessary. It’s also important to regularly review connected apps and services, removing any you no longer use or trust to keep your data exposure to a minimum.
Use a VPN
Using a virtual private network (VPN) hides your real IP address by routing your traffic through a VPN server. This adds an extra layer of privacy and makes it harder for attackers to link your online activity to your physical location. Combined with limiting what personal information you share online, a VPN can strengthen your overall protection against swatting.
An IP address typically reveals only a broad geographic area, such as a city or ZIP code, rather than a precise location. However, websites and online services routinely log IP addresses alongside activity data. Data breaches sometimes expose these logs, underscoring the importance of hiding your IP address to minimize your digital footprint.
Secure your accounts
Your personal data can be exposed if potential swatters gain access to your accounts. These steps make that much harder:
- Use strong, unique passwords: Passwords should be at least 12 characters long and contain a mix of letters, numbers, and symbols.
- Use a password manager: A password manager like ExpressKeys can instantly create strong passwords for all your accounts and store them in an encrypted vault.
- Enable two-factor authentication (2FA): Activate 2FA on your accounts wherever possible. Even if a password is stolen, 2FA can help prevent unauthorized access by requiring an additional verification step.
- Use automatic updates: Automatic software updates help protect your devices from security vulnerabilities that attackers can exploit to access your accounts.
- Install an antivirus program: Setting up reputable antivirus software helps detect and block malicious downloads and malware that could compromise your devices and be used to steal personal information.
- Update privacy settings: Set each of your social media accounts to the highest privacy level to limit public access to your information.
Steps unique to content creators and streamers
Content creators and streamers often have higher public profiles, which can increase their risk of swatting. To protect your personal information on platforms like Twitch, YouTube, Kick, TikTok, and Instagram, try these practical steps:
- Separate public and private accounts: Use different emails, usernames, and profiles for personal activities and public content to avoid linking your online presence to your real identity or location.
- Limit real-time sharing and use stream delays: Avoid sharing your exact location, schedule, or plans during live streams. Adding a short delay between what’s happening live and what viewers see gives you time to prevent accidentally revealing sensitive info. For example, if you notice something personal showing on camera, you can quickly cut or edit it before viewers see it.
- Remove identifying details: Check your stream’s background, overlays, and profile for anything that might reveal where you live or other private info. Remove or blur these details to keep your location private.
- Use moderation tools: Take advantage of built-in chat filters and moderation bots on platforms like Twitch, YouTube, Kick, TikTok, and Instagram to block threats and harassment before they reach you or your audience.
- Document and report suspicious behavior: Save screenshots and records of any threats or harassment, including usernames and timestamps. Report these incidents through the platform’s tools and alert law enforcement if necessary.
- Review privacy settings regularly: Platforms have privacy options that can limit who sees your information and interacts with you. Keep these settings up to date to reduce your exposure. Learn more in our complete guide to TikTok and your location data.
These steps make it harder for attackers to gather the information they need to target you with swatting or doxxing attempts.
Secure your smart home devices
Unprotected Internet of Things (IoT) devices, such as cameras, microphones, smart doorbells, and connected appliances, can be exploited by attackers to facilitate swatting incidents. The FBI has reported that compromised devices have been used to livestream police responses or even to communicate with law enforcement, helping to make false emergency calls more credible and targeted.
Unauthorized actors who gain access to these devices may also be able to learn about your home layout and daily routines or overhear conversations, which can increase the risk of swatting or other privacy invasions.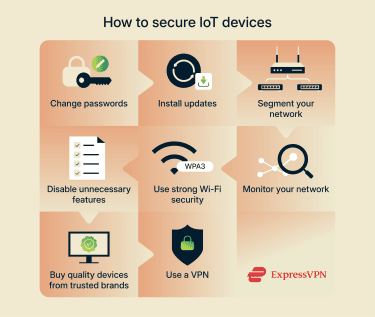
Here are some key steps you can take to secure your smart home devices:
- Keep devices updated: Where possible, regularly install firmware and software updates to patch known vulnerabilities.
- Change default passwords: Use strong, unique passwords for each device to prevent unauthorized access.
- Review privacy and security settings: Disable features you don’t use (like remote access, location tracking, or voice activation), control who can access your devices remotely, and limit permissions where possible.
- Segment your network: Place smart devices on a separate network from computers, phones, and other sensitive systems.
- Use a VPN on your router: Many smart home devices lack native VPN support, but securing your network with a VPN on your router encrypts all traffic from connected devices. This helps protect data as it travels over the internet and adds an extra layer of privacy for your smart home.
- Choose reputable brands: When buying IoT devices, prefer manufacturers known for security, regular updates, and clear support policies.
- Monitor for unusual activity: Check device logs or notifications for signs of unauthorized access or tampering.
For more guidance, see our article on IoT device security.
Apply for a swatting registry
Some local law enforcement agencies and 911 dispatch centers offer ways for residents to share their contact information, concerns, and context proactively. For example, certain cities have developed opt‑in systems that allow individuals who believe they may be at heightened risk of swatting to provide relevant details in advance. When a call involving that address comes in, dispatchers can take extra steps to verify the information before deploying a full tactical response.
If your local agency doesn’t advertise a formal program, you can still contact non‑emergency law-enforcement channels to inform them of any threats, patterns of harassment, or online activity that may put you at risk. Providing context ahead of time (including common online handles, contact details, and known threats) may help dispatchers and responding officers better assess calls involving your address.
Because practices vary by jurisdiction, check with your local police department or emergency communications center to understand what options are available in your area.
What to do if you get swatted
If you’ve been swatted, it's important to take control of your digital privacy as quickly as possible to prevent further exposure. Follow these steps to mitigate the damage:
- Review and secure your accounts: After the incident, change your passwords, especially for accounts linked to your real identity or location. Enable 2FA wherever possible to prevent unauthorized access.
- Alert relevant parties: If you believe any personal information was compromised during the swatting attack (such as your address or other sensitive data), contact your bank, financial institutions, or other relevant organizations to report the breach.
- Monitor for further incidents: Use dark web monitoring services to check if your personal data has been exposed.
- Seek professional advice if needed: For ongoing legal, technical, or emotional support, consider consulting professionals who can assist with the recovery process.
FAQ: Common questions about swatting
What’s the definition of swatting?
Swatting is the act of making a false emergency report to send armed police units to someone’s address. It typically involves claiming a serious threat, like a hostage situation or active shooter. The goal is to intimidate, harass, or endanger the target, often in response to online conflicts.
Why is swatting a crime?
Swatting is illegal because it endangers lives and wastes emergency resources. Making a false report to law enforcement can put both the target and officers at risk. Legal systems treat it seriously due to the potential for injury, trauma, or property damage. Even if no one is physically hurt, the act itself can lead to criminal charges.
How can I protect my IP and identity?
Using a VPN is one way to shield your IP address. A VPN routes internet traffic through a VPN server, making it harder to trace your connection back to your real location. Additional steps to help protect your location information and prevent swatting or doxxing include limiting what personal information you share online, using strong passwords, and adjusting privacy settings on social accounts.
What precautions can streamers take?
Streamers can reduce their risk of swatting and protect their personal information by separating their personal and public accounts, adding delays to live streams, and removing identifying background details. It’s also a good idea to use chat moderation tools, monitor messages for threats, and document and report suspicious behavior.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN