Network topology: Best practices for modern networks
A well-designed network starts with a clear understanding of its structure. Network topology is the blueprint of how devices and connections interact, and it plays a key role in determining a network’s performance, scalability, and security.
This article will explain what a network topology is, guide you through the different types, and provide insights to help select the most effective and secure model for your organization.
What is network topology?
Network topology is a key element of network architecture. It refers to the way a network is arranged, encompassing the physical layout of cables and equipment as well as the logical flow of data.
Common topologies include point-to-point, star, bus, ring, mesh, and hybrid designs. Each type varies in terms of cost, scalability, performance, and reliability. Likewise, there are distinct risks and vulnerabilities associated with various network topologies.
Definition and core concepts
A topology defines the rough shape of a network. The term can be applied to home Wi-Fi, peer-to-peer (P2P) networks, and larger wide area networks (WANs). Topology underpins how networks are built and maintained.
The concept can be divided into two distinct categories: physical and logical.
Physical vs. logical network topology
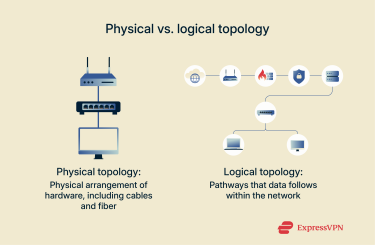 Physical topology refers to the physical arrangement of devices and connections in a network. This includes nodes, such as computers, servers, and printers, and links, which are the cables or wireless connections that connect them. Network devices like switches, routers, and hubs facilitate communication between nodes. The layout of these components affects how complex it is to set up and maintain a network, as well as its speed, reliability, and overall efficiency.
Physical topology refers to the physical arrangement of devices and connections in a network. This includes nodes, such as computers, servers, and printers, and links, which are the cables or wireless connections that connect them. Network devices like switches, routers, and hubs facilitate communication between nodes. The layout of these components affects how complex it is to set up and maintain a network, as well as its speed, reliability, and overall efficiency.
Logical topology, in contrast, describes how data flows through the network. It determines the paths that packets take and influences performance, security, and how network traffic is routed and managed.
Key differences explained
Physical and logical topologies serve different purposes. The physical arrangement determines installation requirements such as cable length and port count and influences real-world maintenance.
Logical topology governs how devices share media and access the network, such as whether devices broadcast on a shared network or take turns sending communication tokens. The type of logical topology you choose will affect your network’s latency and throughput.
When designing a network, admins must consider both physical and logical perspectives. Knowing the cost of cabling and maintenance can be just as important as knowing how your data is managed.
Real-world applications in LAN and WAN
In the local area networks (LAN) that most home users set up, simple topologies are common. Home users and small offices typically use star networks, connecting every device to a central switch. Star networks are easiest to manage but very difficult to scale up if you need to cover a larger area and more devices.
Wide area networks (WAN) deployed by businesses and public entities often use more resilient topologies. Mesh networks, for example, provide redundant paths and support reliable long-distance communications. More complicated topologies are trickier to manage but better at providing reliable coverage to a larger area.
Essential components of a network
Regardless of specific topology, networks consist of nodes and links.
Nodes (devices)
In network topology, nodes are devices that consume data. This includes end-user devices like computers and phones, as well as network hardware like switches, routers, and sensors. Switches forward frames within a network segment, while routers connect separate networks and make routing decisions. Internet of Things (IoT) sensors and actuators collect or act on data, and gateways (typically routers and modems) bridge these devices to the broader network.
Links (connections)
Links connect nodes and provide pathways through which data can travel. This can take the form of physical cables or wireless channels like Wi-Fi and Bluetooth. Wired connections (like Ethernet) offer higher speeds but require physical installation. Wireless links add flexibility and mobility but can be affected by radio conditions and may not support high bandwidth. Links can be point-to-point, point-to-multipoint, or, as in a mesh network, many-to-many.
Learn more in our detailed guide to network connections.
Why is network topology important?
Topology matters because it affects network speed, reliability, scalability, security, cost, and ease of management. A well-designed topology facilitates smooth data flow, can adapt to growth, and resists faults and attacks.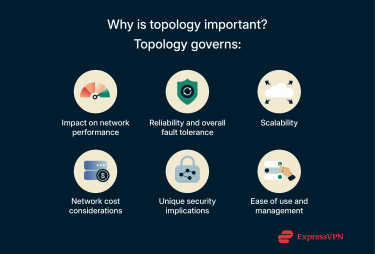
Impact on network performance
Topology has an effect on the latency users experience and a network’s overall performance. For example, in a star network, all traffic goes through a central switch, so an overloaded or misconfigured switch can result in slower speeds across the network. Factors such as the number of devices a packet must pass through, the distribution of traffic across links, and the organization of connections all affect latency and overall throughput.
Reliability and fault tolerance
Some topologies handle faults better than others, reducing the risk of outages.
Redundant paths and backup equipment help minimize disruptions by ensuring that data can always reach its destination. Designs with redundancy generally experience less downtime, as a disruption might not necessarily take down the whole network.
The key to enhancing reliability is avoiding single points of failure. This is affected by topology but can also vary between networks of the same type.
Scalability and flexibility
Scalability is an important factor when choosing a network topology. Though much more important for organizations, it’s still something that home users may need to consider. If you’ll need to update your network to cover a wider area or accommodate new devices and users in the future, note that it’s easier with some topologies than others. Star and tree networks tend to excel in this area, while bus networks present serious challenges.
Admins also need to consider the feasibility of adapting their network to incorporate new hardware or adjust to changing conditions. Networks that are tightly coupled or limited by shared media may create bottlenecks when new applications or devices are added. In contrast, modular designs with clear hierarchical layers are generally much more flexible.
Cost considerations
The cost of running a network covers more than just the price of cables, hardware, and switches. Maintenance is a long-term expense that needs to be taken into account when setting up a network.
Complex topologies with multiple paths deliver high reliability but demand additional hardware, require maintenance specialists, and see increased power consumption, all of which can be costly.
Security implications (conceptual risks)
Topology dictates how data travels, which in turn affects where attackers may find potential entry points. No design is immune to attack, but some arrangements create fewer opportunities for spying or sabotage. More centralized topologies may allow for more focused security, but they also concentrate risk at a single hub, meaning one lapse may have a larger impact. Decentralized or redundant designs distribute risk but are more complex to secure.
When it comes to security, no single topology clearly outshines the rest. The important thing is knowing where your chosen design’s weak points are and taking steps to reinforce and account for them.
Ease of management and troubleshooting
Efficient management and troubleshooting require that a network be logically organized. When this is the case, solving problems and applying updates becomes much easier. Centralized networks are easier to manage and configure, but self-healing properties can result in distributed networks experiencing fewer problems that require manual fixes. Regardless of the specific topology, if a network is well documented, management and repair become much easier.
Types of network topologies
Different topologies suit different use cases. Understanding their strengths and weaknesses helps you make informed choices.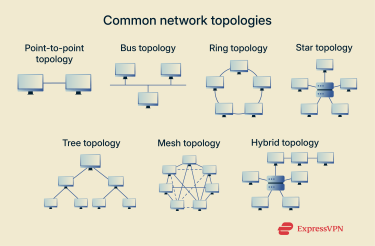
Point-to-point topology
Point-to-point networks have just two devices connected by a single link. With no other nodes sharing the medium, there is no competition over bandwidth.
This topology offers high performance and is straightforward to configure because there is only one path. The drawback is that point-to-point links are not scalable; they serve only two endpoints and cannot be expanded without adding additional links. This can be a good arrangement for linking two larger networks, but the topology is seldom used on its own these days.
Bus topology
In a bus topology, all devices are connected to a single cable known as a backbone. Signals travel along the cable, and each device inspects the frames to see whether they are addressed to it. Bus designs are simple and cost-effective because they require minimal cabling and no central device.
The primary downside is that bus networks do not scale well. As more devices connect, delays and collisions (incidents where two devices send data at the same time) increase. A break anywhere in the backbone brings down the entire network, and troubleshooting can be difficult. As a result, bus topologies are rarely deployed anymore outside of rare circumstances.
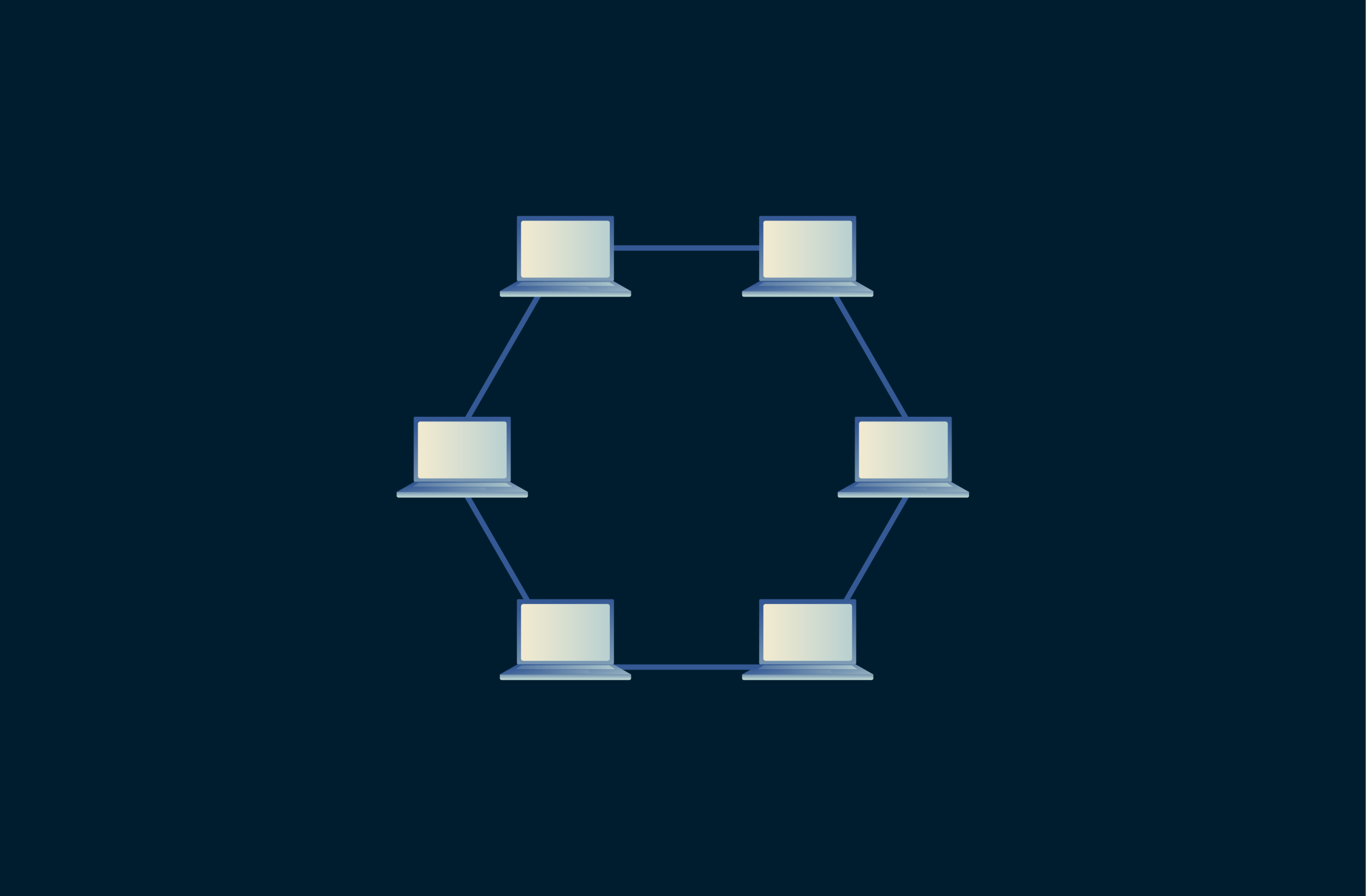
Ring topology
Ring networks form a closed loop in which each device connects to two neighbors. Data travels around the ring until it reaches its destination. Ring topologies are used in token passing protocols where a token circulates among devices to control who can transmit.
Historically, ring topology was used in Token Ring LANs and Fiber Distributed Data Interface (FDDI) networks. In older ring implementations, delays were common as each device would need to wait its turn before sending data. Additionally, a single node failing could disrupt the whole network. Like the bus design, few networks in modern times are built using a true ring topology.
Star topology
In a star topology, each device is linked to a central switch or router. Before the 1990s, most networks had a hub at the center. There are technical distinctions between hubs and switches, but virtually all modern star networks now use switches or, in the case of home networks, routers. That said, the word "hub" is sometimes used colloquially to refer to switches.
In any case, data in a star network travels to the central switch, which then forwards it to the destination. This arrangement isolates node failures because a broken cable affects only one device.
The main vulnerability is the central hub; if it fails, all communications stop. Star networks are also only scalable to a limited degree. The central switch can only handle a limited number of connected devices, creating a bottleneck. That said, mixing star and tree networks makes for a topology that is much easier to expand to larger sizes.
Tree topology
It’s best to think of a tree topology as multiple star networks connected together in a larger star configuration. Nodes are arranged in layers, starting with a root node that connects to intermediate nodes, which connect to lower-level devices.
Each branch can operate independently, so a failure in one branch does not necessarily disrupt the rest of the network. Tree structures are widely used in enterprises where departments or floors have their own star networks connected by a hierarchical backbone. This topology scales well and supports structured growth, but networks of this type can be very difficult to optimize. Additionally, the existence of multiple single points of failure raises reliability concerns.
Mesh topology
A highly decentralized design, mesh networks are flexible and resilient. In a full mesh setup, every node connects directly to every other node, providing multiple independent paths for data. This results in high redundancy and fault tolerance but requires many connections, which increases cost and complexity.
In partial mesh networks, only some nodes are connected to all others. This reduces redundancy but also costs. In either case, wireless mesh networks are easy to scale; expanding the coverage area can be as easy as plugging in a new node.
Mesh networks are increasingly popular in large homes to eliminate Wi-Fi dead zones.
Hybrid topology
Hybrid topologies combine two or more base topologies to support large and complex networks. Common examples include star-ring and star-bus networks. They are deployed when a single topology can’t meet a network’s requirements, such as a large organization with a lot of users and heavy traffic.
A hybrid design can improve fault tolerance and simplify the process of adding or removing network segments. This approach allows admins to combine other topologies in unique ways, which can improve reliability at the cost of added complexity.
Hybrid architectures are often more reliable. If something fails, other parts may continue to function. In practice, most larger networks are, at least in part, hybrids.
Network topology diagrams and mapping
A topology diagram is often included within a broader network map to show how devices are connected, and it’s an important step for most admins.
What is a network topology diagram?
A topology diagram is a map that shows all devices and connections within a network. A complete diagram will represent both physical and logical structures. Creating and revising a topology diagram is important; this kind of visual aid can provide valuable assistance at every stage, from initial planning to troubleshooting and ongoing maintenance.
How to create a network topology diagram
Start by deciding how your diagram will visually represent the network. While there’s no universal standard, most practical diagrams use a combination of Cisco’s standardized icons and sometimes Unified Modeling Language (UML) symbols. In scientific or theoretical contexts, graph theory notation is common. Whatever approach you choose, maintain consistent symbols throughout the diagram.
For smaller networks, a simple key may suffice. Circles and squares can represent nodes, lines for links, triangles for wireless access points, and double circles for gateways. You can manually list all routers, switches, servers, firewalls, wireless access points, and endpoints, then indicate how each connects.
Admins for smaller systems may be able to list all devices within a network manually. One might choose to list all routers, switches, servers, firewalls, wireless access points, and endpoints, then note how they connect to each other.
For larger or more complex networks, automated tools are recommended. These tools can detect devices, IP addresses, and links in real time, producing accurate diagrams with consistent symbols. Even with automation, double-check that your inventory includes network addresses, virtual local area networks (VLANs), and external connections, and account for isolated or firewalled devices that some tools may miss.
Best practices for diagramming
- Use consistent symbols: Choose industry-standard icons for routers, switches, firewalls, and other devices so that anyone reading the diagram can understand it.
- Keep diagrams simple: Group related devices and focus on relevant connections to avoid clutter. Overcrowded diagrams can be confusing. A simple diagram makes problem-solving easier.
- Keep labels clear: Annotate links with unique but readable and easily understandable labels. Clear labels reduce errors during troubleshooting.
- Document all connections: Include wired and wireless links, remote access paths, external connections, and network devices to ensure completeness.
- Update regularly: Schedule regular reviews to keep diagrams current. Outdated information can make a diagram practically useless.
- Collaborate: Share diagrams across teams and accept feedback on how to better represent real network conditions. The goal should be to ease confusion as much as possible.
Common mistakes to avoid
- Excessive or insufficient level of detail: The purpose of a diagram will dictate the appropriate level of detail. Leaving out elements will take away from a diagram intended to offer a full picture of a network to aid troubleshooting, while overcrowding can overwhelm readers if a diagram is only intended to be a general reference.
- Non-standard icons: Using idiosyncratic symbols makes diagrams hard to interpret; stick to common shapes.
- Outdated information: Failing to update diagrams after changes leads to confusion and makes your diagram inaccurate and therefore unhelpful.
- Ignoring remote networks: Omitting elements like virtual private networks (VPNs), cloud connections, and remote access leaves an incomplete picture.
- Not verifying diagrams: Failing to compare diagrams with actual configurations can result in misleading representations of a network.
Practical applications of network topology
Here are several examples of how computer network topology comes into play in the real world.
Business and enterprise networks
Enterprises use topologies that balance performance, reliability, and manageability. Star topologies are often used for smaller offices, while larger networks employ tree networks to isolate faults and support easy expansion.
In larger organizations, branches of star networks may connect via a hierarchical tree backbone or a partial mesh to provide redundancy and segment traffic. A well-designed topology supports productivity by reducing downtime and simplifying the application of security policies.
Data centers and cloud infrastructure
Data centers require highly scalable and low-latency networks. Traditional designs use a three-tier network architecture with core, distribution, and access layers.
The core layer provides high-speed forwarding between distribution layers and external networks. The access layer connects directly to servers and allows for communication with the network. The distribution layer aggregates access from switches and enforces security rules.
Modern data centers use topologies capable of supporting massive traffic flows, providing redundancy, and scaling horizontally through spine-and-leaf architectures.
Internet of Things (IoT) and smart device networks
IoT deployments often involve many low-power devices spread over wide areas. Mesh networks are a popular choice in such environments because they let devices relay traffic for each other, increasing coverage and resilience.
Low-power wide-area technologies such as long-range wide area network (LoRaWAN) use a star-of-stars topology: end devices send data to gateways that forward it to a central network server. Other IoT networks use personal or local area technologies like Bluetooth or Wi-Fi, depending on range, power, and bandwidth requirements. Selecting an IoT topology involves balancing power consumption, coverage, and management complexity.
Security applications (real-world use cases)
Network topology affects security because it determines how traffic flows and where vulnerabilities lie. The following real-world use cases show how segmentation strategies can protect networks:
- Demilitarized zone (DMZ) segmentation for internet-facing services: Organizations that rely on web or proxy servers limit damage from data breaches by placing those servers in a separate DMZ. Implemented on hardware separate from the main network, the DMZ enables communication between protected resources and public-facing internet traffic.
- Internal segmentation firewalls for departmental networks: Companies deploy internal segmentation firewalls to divide corporate networks by department or function. Segmentation limits lateral movement by threat actors like botnets and increases visibility.
- Software-defined networking segmentation (SDN): Manufacturing and utility networks may use SDN to create multiple virtual networks. An operational technology SDN (OT-SDN) controller centrally manages these segments and can help enforce zero-trust rules. This enhances overall security and can be a step towards achieving zero-trust network access.
How to choose the right network topology
There’s no one-size-fits-all solution, so it’s important to consider your specific needs.
Factors to consider before choosing a topology
There are several factors that will determine the ideal topology for a given network. You’ll need to consider size, budget, performance, security, flexibility, and maintenance.
Size and scale of the network
The size of a network dictates which topologies are practical. A small office can use a single switch in a star configuration, but this topology becomes highly impractical as the coverage area expands and more devices are added. As an organization grows or spreads across multiple locations, a hierarchical tree, mesh, or hybrid topology provides better segmentation and scalability.
Budget and cost efficiency
Star topologies have lower hardware costs because they use fewer cables and devices. Mesh and hybrid designs offer high performance and customization but require more investment in switches, ports, and cabling. Evaluate the total cost of building a new topology, including maintenance and potential network downtime.
Performance and reliability needs
High-performance networks often use star or mesh architectures. Star topologies won’t go down unless the central component is damaged. Mesh networks offer multiple paths for critical traffic to create redundancy, helping improve reliability and performance.
By contrast, bus and ring topologies can suffer from network congestion or complete outages if a single component fails. Hybrid designs can balance these characteristics but are more complex and require more maintenance.
Security requirements
A secure network topology minimizes unnecessary exposure to risk. Avoid designs where sensitive traffic shares media with untrusted devices. You should implement segmentation and use firewalls to separate sensitive traffic.
Regardless of topology, encrypting Domain Name System (DNS) traffic with a VPN or other method is also a good idea. With this protection, anyone intercepting network data won’t be able to read it.
Ease of maintenance and troubleshooting
Star and tree topologies simplify maintenance because each connection is distinct and faults are easy to isolate. Bus and ring designs are harder to troubleshoot because a single failure can take down the network, and fixing the break can be complex or time-consuming.
Mesh and hybrid networks require skilled personnel to operate due to their greater complexity, for example. Redundancy in mesh topologies improves resilience but can also make it more difficult to isolate faults. Overall, it’s best to choose a topology that matches your team’s expertise level.
FAQ: Common questions about network topology
What are the main types of network topology (and how are they used)?
The main physical topologies are bus, ring, star, mesh, tree, point-to-point, and hybrid. Regardless of type, the topology will dictate how physical infrastructure is arranged and how data moves about the network.
Which network topology is the most secure?
No topology is inherently secure, but some offer advantages. Each topology handles security differently; for example, star networks have a central switch, so securing that device is vital. Regardless of topology, your network security depends on proper segmentation, encryption, and access controls.
Which topology is best for small businesses or large enterprises?
For small businesses, star topologies work well because they’re simple to deploy and manage. But star networks can only be scaled so far, so they become impractical past a certain point.
For large enterprises, tree topologies provide better scalability and manageability. Mesh segments may be used to cover hard-to-reach areas and can reduce downtime. Hybrid models are cost-effective and flexible but can be easily misconfigured to create network issues. The choice ultimately depends on budget, growth plans, and security requirements.
How do different network topologies affect performance?
Performance is affected by both topology and use case. Factors such as the number of endpoints and bandwidth matter regardless of topology. For example, networks built around a star design can experience reduced speeds if the switch is congested. Distance from the gateway can also be a factor, though this is less of an issue with mesh networks.
When should I switch or upgrade my network topology?
You should reconsider your topology when your network has persistent performance issues, experiences frequent outages, or when your business requirements change, whether due to evolving practices, physical expansion, or regulatory shifts.
How does VPN affect network topology and security?
A VPN overlays an encrypted tunnel on top of your physical and logical topology. It doesn’t change how devices are wired, but it routes your traffic through a secure server and encrypts it. This logical overlay prevents unauthorized users from reading your traffic and hides your IP addresses.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN